Research Article, J Comput Eng Inf Technol Vol: 8 Issue: 3
Cloud Computing Survey on Services, Enhancements and Challenges in the Era of Machine Learning and Data Science
Wajid Hassan1*, Te-Shun Chou2, Omar Tamer3, John Pickard2, Patrick Appiah-Kubi4 and Leslie Pagliari2
1Indiana State University, Terre Haute, Indiana, USA
2East Carolina University, Greenville, North Carolina, USA
3CalPoly Pomona, Pomona, California, USA
4University of Maryland University College, Largo, Maryland, USA
*Corresponding Author: Wajid Hassan
Indiana State University, Terre Haute,
Indiana, USA
Tel: (410) 603-4767
E-mail: wajidhassan@yahoo.com
Received: March 19, 2019 Accepted: August 18, 2019 Published: August 26, 2019
Citation: Hassan W, Chou T, Tamer O, Pickard J, Appiah-Kubi P, et al. (2019) Cloud Computing Survey on Services, Enhancements and Challenges in the Era of Machine Learning and Data Science. J Comput Eng Inf Technol 8:1.
Abstract
Cloud computing has sweeping impact on the human productivity. Today it’s used for Computing, Storage, Predictions and Intelligent Decision Making, among others. Intelligent Decision Making using Machine Learning has pushed for the Cloud Services to be even more fast, robust and accurate. Security remains one of the major concerns which affect the cloud computing growth however there exist various research challenges in cloud computing adoption such as lack of well managed Service Level Agreement (SLA), frequent disconnections, resource scarcity, interoperability, privacy, and reliability. Tremendous amount of work still needs to be done to explore the security challenges arising due to widespread usage of cloud deployment using Containers. We also discuss Impact of Cloud Computing and Cloud Standards. Hence in this paper, a detailed survey of cloud computing, concepts, architectural principles, key services, and implementation, design and deployment challenges of cloud computing are discussed in detail and important future research directions in the era of Machine Learning and Data Science have been identified.
Keywords: Wajid Hassan1*, Te-Shun Chou2, Omar Tamer3, John Pickard2, Patrick Appiah-Kubi4 and Leslie Pagliari2
Introduction
As stated by the IEEE Computing Organization, “The goal of computing services is to enable IT services and computing technology to perform business services more efficiently and effectively.” NIST, The National Institute of Standards and Technology suggests [1] [2] that models of cloud computing are “composed of five essential characteristics.” (Mell and Grace) The characteristics are: service measurability, broad network access, resource pooling, rapid elasticity and on-demand self-service. Each of these aspects is very important to the Cloud Technology. Cloud computing service features are shown in Figure 1 and will be discussed in the paper later.
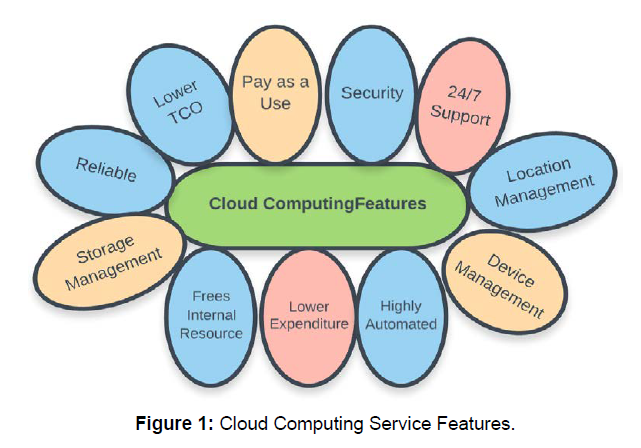
Figure 1: Cloud Computing Service Features.
There is massive information on the Cloud Computing in terms of research papers, white papers, blogs and articles that all the information cannot be covered in one paper. Hence, this survey paper provides an in-depth knowledge of a few research papers, rather than wide range of papers with shallow coverage. Therefore, this survey offers readers a fair understanding on the past, present and future of cloud computing. Cloud computing offers a number of deployment models, each of the models has its pros and cons. A brief comparison of the computing layers is given below. The impact of Cloud computing is enormous; with cloud computing small businesses can go global very easily. Developing countries have already shown the potential of new markets and have emerged as new competitors. Cloud computing gives companies and individuals smarter ways to develop products, collaborate and test ideas cheaply and rapidly. One more common example is the usage of blackboard that is used by schools, colleges and universities around the world, all these blackboard systems store the data in the cloud and make attending school much easier. With Cloud’s massive computation power language barriers have already faded. There are many security threats [3] linked to hosting numerous users and information storage in cloud computing, that can be mitigated by strong security mechanisms of cloud computing to ensure the information isolation of users (Table 1) [4-20]. But this becomes even more complicated [21,22]. By way of instance, a hacker can deploy malicious software within a border node, which consequently could exploit a vulnerability which can hamper the quality of service of their router. Such kind of threats might have a substantial negative effect.
architecture, applications,
and approaches [5]2011Hoang T. Dinh, Chonho Lee, Dusit Niyato
and Ping WangA survey of mobile cloud computing (MCC), for general understanding of the readers, including the definition, architecture, and applications of MCC has been presented in this paper.A Survey on Open-source Cloud Computing Solutions [6]2008Patrícia Takako Endo, Glauco Estácio Gonçalves, Judith Kelner, Djamel SadokThis survey paper discusses and presents open-source solutions for cloud computing.A survey on security issues in service delivery models of cloud computing [7]2011S. Subashini, V. Kavitha The survey paper gives a brief view of current cloud security challenges, risks and imparting the existing methodologies done by the researchers for cloud security. This research work is suggested suitable for beginners as a guideline for pursuing their research in the domain of cloud security. This paper also discusses about data protection and privacy.A Taxonomy and Survey of Cloud Computing Systems [8]2009Bhaskar Parasad, Ian LumbThis paper explains taxonomy of cloud architecture, then use this taxonomy with existing services.ACM Tech Pack on Cloud Computing [9]2015Ajay MohindraHere basics paradigms of Cloud are discussed.Cloud Computing:
Overview & Current Research Challenges [10]2012Mohsin NazirThis paper describes cloud computing, various models of cloud and explains the architecture of cloud computing.Mobile cloud computing: A survey [11]2013Nirosheini Fernando, Seng W. Loke, Wenny Rahhayu.An extensive survey of MCC (mobile cloud computing) is provided in this paper. It also highlighting the security concerns in cloud computing.Survey Paper on Cloud Computing [12]2013Palvinder Singh, Er. Anurag jainThis paper focusses on Cloud Services.Survey Paper on Cloud Computing [13]2010Kalpana Tiwari, Er. Sachin Chaudhary, Er. Kumar ShanuThis survey paper defines Cloud Computing, discusses characteristics and architecture of Cloud Computing in detail, and describes the deployment and service models of cloud computing.5G Internet of Things: A Survey [14]2018Shancang Li, Li Da Xu, Shanshan ZhaoThe IoT solutions face a lot of challenges such as security, large number of node connections and new standards. This survey paper reviews 5G IoT, main challenges and trends in 5G IoT research, and key enabling technologies.A Manifesto for Future Generation Cloud Computing: Research Directions for the Next Decade [15]2018Rajkumar Buyya, et allThis research paper identifies emerging trends, open challenges in the era of cloud computing and impact areas. It also gives direction for the future research in cloud computing.A Survey of Communication Protocols for Internet-of-Things and Related Challenges of Fog and Cloud Computing Integration [16]2018Dizdarević, admela jukan, xavi masip-bruinThis survey paper describes the communication protocols of application layer, which fulfill the IoT communication requirements and discusses their implementation potential in cloud and fog based IoT systems.A Survey on the Edge Computing for the Internet of Things [17]2017Wei Yu, Fan Liang, Xiaofei He1, William Grant Hatcher, Chao Lu, Jie Lin, And Xinyu YangA comprehensive survey has been conducted in this paper; it analyzes how the edge computing is improving the IoT network’s performance. The edge computing based on the architecture is categorized into different groups and their performance is studied by comparing bandwidth occupation, network latency overhead and energy consumption.A Taxonomy of Software-Defined Networking (SDN)-Enabled Cloud Computing [18]2018Jungmin Son, Rajkumar BuyyaDifferent aspects and elements of the SDN based cloud computing have been explained in this research paper. The paper discusses SDN for cloud computing in detail with focus on network virtualization, traffic engineering, data center optimization and security.Augmentation Techniques for Mobile Cloud Computing: A Taxonomy, Survey, and Future Directions [19]2018BOWEN ZHOU And RAJKUMAR BUYYAThis survey paper provides survey of frameworks and existing technologies for cloud computing regarding both storage and computation. The paper focuses on the technical aspects of cloud computing. The objective of survey paper to define the guidelines for adopting cloud computing techniques as well as to define supporting mechanisms such as fault tolerance and decision-making policies for reliable cloud services.Factors influencing the organizational adoption of cloud computing: a survey among cloud workers [20]2018Mark Stieninger, Dietmar Nedbal, Werner Wetzlinger, Gerold Wagner, Michael A. ErskineThe survey paper provides better understanding of the cloud services adoption.From cloud computing to fog computing in Healthcare big data [21]2018Babur Hayat Malik et. allThis research paper characterizes, talks and investigates the various application of fog & cloud computing. It also discusses the impact of fog & cloud computing on healthcare big data.Future Edge Cloud and Edge Computing for Internet of Things Applications [22]2017Jianli PanThis research paper discusses IoT applications which benefit from edge cloud, key enabling technologies, research topics and research efforts in edge computing. It draws an overall picture of future research directions and the ongoing research efforts in edge computing.Next Generation Cloud Computing: New Trends and Research Directions [23]2017Varghese, Rajkumar BuyyaThe research paper describes the cloud computing infrastructure and the infrastructure use by multiple providers and discusses the benefits of decentralizing the computing away from the data centers. Need of new computing architecture is arising due to new trends being discovered in cloud computing. According to anticipation, the new architectures will impact areas such as data intensive computing, self-learning systems, connecting devices and people and service space.Security and Privacy Issues of Fog Computing: A Survey [24]2018Shanhe Yi, Zhengrui Qin, and Qun LiIn this paper, the challenges and corresponding solutions of fog computing are presented in a brief manner.Survey of Cloud Computing and its Application [25]2018G Likitha Reddy and B. S. S. Murali KrishnaThe focus of the research paper is distributed computing systems and discusses the issues in expanding the software engineering territory.Survey of Machine Learning Algorithms for Dynamic Resource Pricing in Cloud [26]2018Meetu Kandpal, Dr. Kalyani PatelThe paper provides insights of various machines learning algorithm that could be helpful in deriving the dynamic pricing of resources in cloud.Survey on Cloud Computing Services and Challenges [27]2018C. Ranjith KumarThis survey paper describes in detail the several system providers of cloud computing and discusses the privacy and security concerns in cloud computing.
Table 1: Important contribution of Survey Papers on Cloud Computing.
Furthermore, if user-specific data has to be temporarily saved on multiple border locations to ease computing on the border, then privacy problems together with security issues need to be dealt with and this is done by cloud computing security mechanisms. Another active area of interest is encryption & decryption mechanics that are energy intensive and resource hungry and can use the large-scale nature of dispersed clouds. One another area of active research is the approach to detect intrusion, for example, using anomaly detection but this will have to be built for real time attacks consuming enormous amount of resources and bandwidth, and this becomes more challenging in a restricted environment for upcoming IoT workloads. Cloud computing is cost effective if the cloud environment is deployed correctly, but there are lots of challenges faced in deploying it right. Cloud usage can prove to be very expensive for small enterprises which are relying solely on Public Cloud Computing infrastructure, hence with pay-as-you-go and on demand cloud services, the service level agreement and assurance that service levels are being met hold a critical importance. A lot of research activity is hence derived based on the Cloud computing economics and pricing, negotiating billing and service-level agreements with cloud providers, Cloud monitoring & management and Cloud disaster recovery. We will discuss these in the upcoming sections. This survey paper is organized as follows: In section 1, an introduction to cloud computing is presented; section 2 gives an overview of survey papers published on cloud computing, section 3 describes the architecture of cloud computing, section 4 discusses the cloud computing service models, section 5 describes the deployment models of cloud, section 6 discusses cloud computing open architecture, section 7 defines cloud storage models, section 8 discusses about virtualization in cloud computing, in section 9 various cloud service providers have been described, section 10 gives an overview of open source virtualization platform for private cloud, in section 11 various cloud security risks have been discussed, section 12 identifies recent technology trends in the era of cloud computing, section 13 describes the challenges in cloud computing, section 14 gives an overview of Laws, policies and regulations in cloud computing, section 15 discusses the upcoming cloud computing technologies, section 16 discusses our future work in this area and section 17 concludes the paper (Table 1) [23-27]. Our contribution to Cloud Computing is unique as it discusses the current challenges and offers insight into the future that will mitigate these challenges.
Background Work
The study of cloud computing ecosystems is a favorite topic of researchers because of the evolving nature of Cloud Computing. Many of these survey papers are obsolete even before their publication due to the ever-expanding use cases and deployment techniques. Cloud computing has many dimensions, use cases, implementation practices and impacts a variety of user. The chart below provides the important contribution done by a select few survey papers in recent past.
Cloud Computing Architecture
The architecture of cloud computing refers to different components which make up the cloud system in terms of databases, software capabilities and applications etc., designed to deliver the power of cloud resources for solving problems of business. The complete architecture of cloud computing is engineered to provide users with network security, uninterrupted services and high bandwidth.
Different cloud-based services have their distinct and unique and distinct cloud architectures. The generic cloud architecture is shown in Figure 2 that shows basic elements of the cloud computing Architecture including Infrastructure, Storage, Service, Application, Management and Security components.
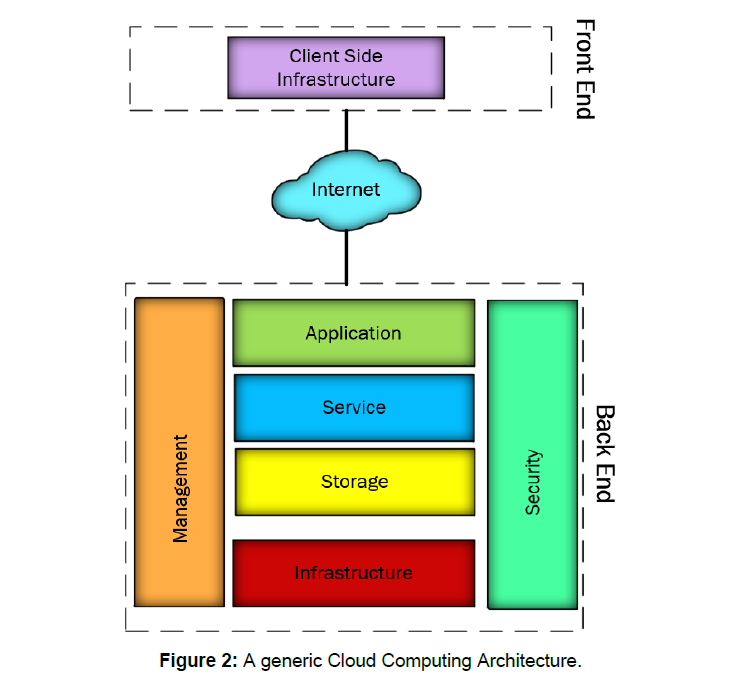
Figure 2: A generic Cloud Computing Architecture.
Service Models
The service models of cloud computing represent different delivery models of cloud that are used with the deployment models of cloud. The service models of cloud are the Software as a Service (SaaS), Platform as a Service (PaaS) and Infrastructure as a Service (IaaS) (Figure 3) shows the necessary classification of the roles that one particular service model fulfills. The example of each of the service model is given in Table 2. Figure 3 describes the responsibility and management of the cloud user and cloud provider managing distinct components of the offering.
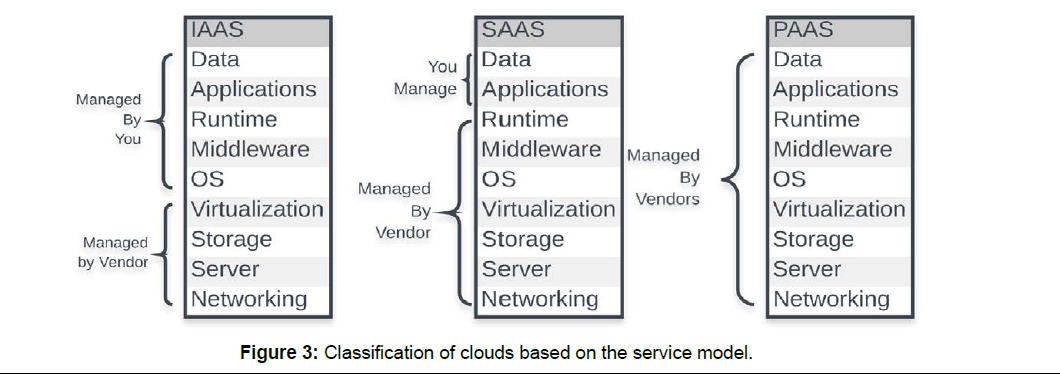
Figure 3: Classification of clouds based on the service model.
(IAAS)Complete applications that are customized and rentedAmazon Web Services,
Window AzurePlatform as a Service (PAAS)The developer platform that abstracts the OS, infrastructure, and middleware to drive the productivity of developerRed Hat OpenShift, HerokuSoftware as a Service (SAAS)A distribution model in which host applications are made available to the users over internet by the third partyGoogle Docs,
Google Sheets;
Salesforce.com, InsightlyDesktop as a Service (DaaS)Complete applications that are customized and rentedCitrix, VMware
Table 2: Example of Cloud Service Provider based on the Service Model.
Infrastructure as a service (IaaS)
This is the lowest level of service provided to cloud user with greatest flexibility [28] where the cloud users are provided controlled access to the hardware infrastructure. The user can deploy operating system and application software of their choice. The client doesn’t really have the control of the Physical hardware but are free to use the virtualized hardware as they please. Client has to manage most of the security aspects of protecting the infrastructure.
Platform as a service (PaaS)
In the Service Model, Platform Software is already installed for the user of cloud services including Operating System, Storage Drives Controllers, Networking and other required software [29]. User can install the software’s that they need on top of these software’s. The virtual infrastructure and hardware are controlled by the CSP.
Software as a service (SaaS)
SaaS is also called ‘on demand software’. This [30] is a licensing and software delivery model where a fully functional and complete model is delivered on the subscription basis to the users over web. The end users access the SaaS offerings typically through web browser.
Desktop as a service (DaaS)
This is a kind of virtual desktop infrastructure (VDI). The VDI is outsourced & handled by the 3rd party. DaaS [31] is a cloud service delivered frequently along with the applications on the virtual desktop. The user and use cases for each of the Service model are shown in Table 3.
Table 3: Users and Use Cases of Service Models.
Deployment Models
Cloud computing has four deployment models namely: Public Cloud, Private Cloud, Hybrid Cloud and Community Cloud.
Private cloud
As suggested by the name, the private cloud is managed within one organization. Also, it is not mandatory that same organization runs the infrastructure; third party can also manage it. Geographical location [32-34] of cloud can also be away from that managing organization. Briefly private cloud serves single organization and is not consumed by other sources or customers.
Public cloud
The shared computing infrastructure is provided by the public cloud. Its physical infrastructure is embedded within CSP and public can access it. As resources are shared so the users pay according to consumed resources. The physical structure is out of the location. For instance VMs and public storage apps it is a multi-tenant virtualized environment. It refers to the usage of a number of data centers and file replications. It enhances the scalability of different IT resources.
Community cloud
In community cloud a community of users and organizations is created. All resources are shared among different organizations and users [35]. Basically, the terms, security concerns and mission are shared at same level among community formed. Also, it is not mandatory for geographical location to be in the premises of organization.
Hybrid cloud
Just like name, an amalgam of two or more clouds form a hybrid cloud [35,36]. The best feature is that the integrity of each model remains intact while serving some combined functionalities and standard technologies. Hybrid clouds share proprietary technology. Data and applications are shared equally among private and public cloud’s amalgam. Hybrid cloud can handle any overflow without giving access to third party datacenters. It is beneficial in scaling resources.
Cloud Computing Open Architecture
The term Ecosystem is a term which is used to describe system of the components which are dependent on each other working together for enabling the services. In case of the open architecture of cloud computing [37] this complex term not only includes the traditional elements associated with cloud computing like software and infrastructure, but it also includes consultants, integrators, third parties, partners and all other related components. The cloud is an ecosystem of interconnected array of services, resources and applications that provide value for consumers and businesses. The open architecture of cloud computing [38] covers seven principles as shown in Figure 4. The details of each principle are discussed below.
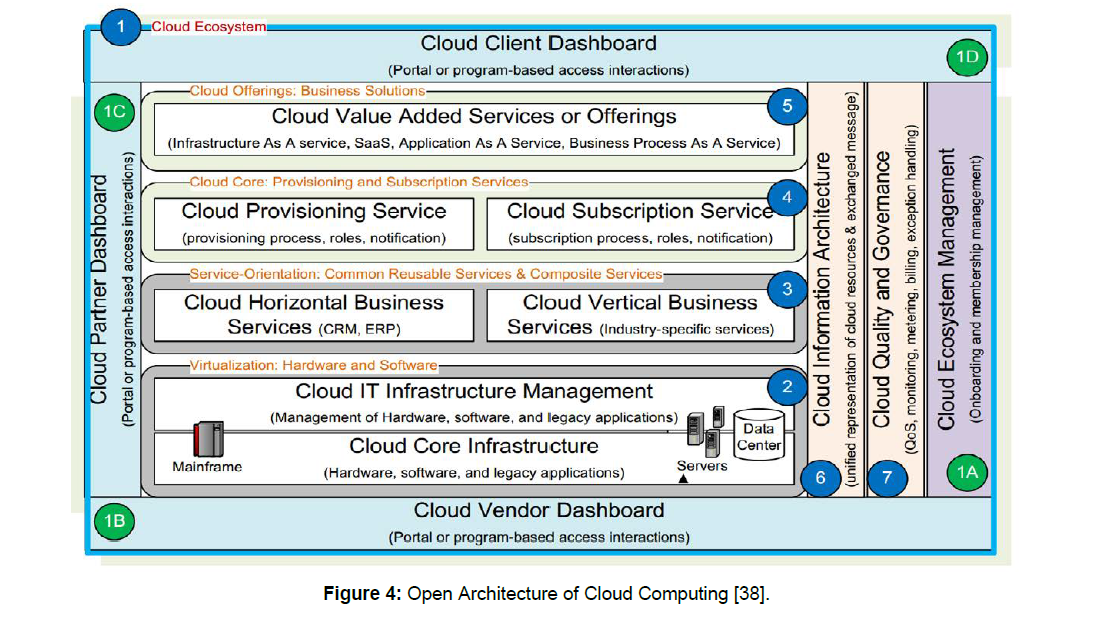
Figure 4: Open Architecture of Cloud Computing [38].
Cloud computing integrated ecosystem management
The cloud architecture must support the ecosystem management of cloud environment. The ecosystem in a cloud environment includes all solutions, involved solution providers, end users and partners which provide shared resources in the environment of cloud. Ecosystem management layer in cloud computing provides common utilities to hosting environment, supports the operations of frontend and provides integrated on boarding processes [38]. It also supports the seamless message exchanges and collaboration among cloud vendors, clients and partners.
Virtualization for cloud infrastructure
The virtualization can be enabled in cloud computing environment by two basic approaches.
(a) Virtualization of hardware used to manage the hardware equipment in plug-and-play mode
(b) Virtualization of software that uses software code virtualization technology or uses software image management to enable the sharing of software.
Service orientation for the reusable services
Another enabling force for cloud computing is service orientation which further realizes the business value from asset reusability, composite applications and mashup services. The common reusable services are of two types:
The Horizontal business services of cloud
It consists of different platform services which hide complexities of middleware, databases and tools.
The Vertical business services of cloud
It includes all domain specific or industry specific services.
Extensible subscription & provisioning
An exceptional feature of a cloud environment is extensible provisioning of service. The provisioning feature can only support only a particular type of resource sharing without extensibility. This also implies that the architecture of service provisioning for free use users and paying users would be same. The service consumers are interested in how easily they can access services based on business logics and their goals.
Cloud offerings
The offerings of a cloud environment are services or final products which are provided by platform of cloud computing. The offerings of a cloud are also referred to as cloud business solution as they address certain business goals. Most of the cloud offerings are accessed through web browser. Examples include infrastructure cloud and storage cloud.
Unified exchange framework and information representation
In order to enable collaborative and effective cloud computing features, the message and information exchange of resources of cloud computing is very important. In open architecture of cloud computing, computing resources include all business entities (e.g. clients, partners and vendors) and supporting resources like virtualization modules, service orientation related modules, cloud core and cloud offerings. The architecture of cloud information flows in a synchronized way to carry out communication among different modules effectively.
Cloud quality and governance
The most important module in open architecture of cloud computing is the cloud quality and governance. This module is responsible for the definition & identification guidelines and quality indicators for cloud to govern the deployment, operation, design, and cloud offerings’ management. The parameters of QoS (quality of service) can be used as quality indicators. The traceability enablement and compliance validation can be used to check the integrity. One important cloud quality aspect is security.
Cloud Storage Models
Different cloud solutions have different cloud storage architectures. The various deployment options include the public, private and hybrid clouds. There are fundamentally three storage architectures for storing the data internally.
Shared file/block storage system
In Shared File Storage model, the files are shared among desired users. Files are split into folders and sub-folders. These are then made available to users through internet. For data storage and accessing the protocol can be any like Common Internet File System (CIFS), Server Message Block (SMB) and network File System (NFS).
Object storage system
In object storage system data is converted into objects to store or to access. Each and every object contains a universal key, Hash, URL under the scenario of web services. Its prime protocol is HTTP. The storage is provided by Cloud Data Management Interface (CDMI).
Database or table storage system
Relational Database Management System (RDBMs) or relational database is the common technique by which majority of industries store data. The storage is in the form of rows and columns. Database major concern is to keep the integrity and mitigate redundancy. However, scalability and performance are other issues.
Virtualization
Virtualization is one of main drivers of Cloud Computing. Virtualization refers to having multiple virtual machines and users on one single server. The key technology enabler of Cloud Computing is virtualization and is present for some time now. Depending on the type of deployment HyperV, Xen [39], VMware, Libvert KVM make the underlying platform for Cloud Computing [40] and hence cloud computing possible. Each of the virtualization techniques is discussed below. Some recent advances in Cloud Technologies have made the cloud services more agile and robust. Docker, Kubernetes, Linux Containers, Virtualization have enabled wide deployment and adoption of fast reliable and scalable clouds. These are discussed below.
Containers
Containers are taking a larger footprint in the cloud computing model. It complements the Virtual Machines. One of the major differences between containers and virtual machine is the abstraction of hosting resources as shown in Figure 5. Containers provide a reasonable packaging mechanism where software may be abstracted in the surroundings where they really run. The decoupling enables container-based software deployment consistently and readily, whether the targeted environment is the public cloud, a personal data center or the personal laptop of a developer. A clear separation of issues is given by containerization, as the programmers focus on dependencies and logic of their application, whereas the groups of IT operations focus on the management & deployment without even bothering about the program details like special configurations and software versions that are specific to program.
Figure 5: The evolving ecosystem of Cloud Computing architecture.
10.2. Linux Containers (LXC)
Linux containers serve as lightweight alternatives to full machine virtualization. Linux offers a powerful API and toolsets for helping users easily manage and create systems or the application containers via Linux containers. The virtual environment of Linux containers has its CPU, own memory, network functionality, block input and output and more. It provides the virtual environment via the group’s features in the Linux kernel. LXC typically offer less isolation than a virtual machine.
Docker (Open source containers)
Docker, open source containers used for automating applications’ deployment as portable, self-sufficient containers which can virtually run anywhere & on any server type. It is lightweight alternative to the virtualization of full machine provided by the traditional hypervisors like Xen, KVM etc. [41] Virtual machines in traditional hypervisors need their own operating systems. But on Docker, container resides on single host OS and applications operate inside this container. This host OS can sever different containers. The support of Docker is being integrated with cloud platform of OpenStack.
Kubernetes (Google container Svc)
An open source platform for automating deployment, management and scaling of the containerized applications is known as Kubernetes. The containers that make up application into logical units for management and easy discovery are grouped in this. Kubernetes has been built upon fifteen years of experience of running the workloads of production at Google, which combined it with best ideas from community and breed practices. Kubernetes was developed by Google which open-sourced the project in 2014. Kubernetes supplies a container-centric direction atmosphere. This provides a lot of the ease of Platform for a Support (PaaS) together with the flexibility of management for a Support (IaaS) and empowers reliability across infrastructure suppliers.
HyperV (Microsoft hypervisor)
Hyper-V manufactured by Microsoft, is a host virtualization product which offers the services of virtualization through hypervisor-based emulations. Hyper-V is a host hypervisor which allows entry of one physical server into several virtual servers; each virtual server shares their host machine hardware resources and is powered by Hyper-V. The function of Hyper-V is both as standalone option and as addition to Windows Server 2008 R2 and is constructed to enhance the utilization of server and decrease funding costs for purchasing in-house server. Hyper-V stipulates basic operation to make the virtualization layer within the surface of the server system also empowers guest operating procedures to be set up & controlled via integrated control console.
Xen (Citrix hypervisor)
An open source server virtualization platform which is based on Xen hypervisor and enables the management & creation of the infrastructure of virtualized server is called Citrix XenServer. It has been built over Xen Virtual machine hypervisor and is developed by Citrix Systems; it provides server virtualization and monitoring services. It can be executed on processors of entire x86 series and is available in 64-bit hypervisor platform. It supports most servers’ operating systems and provides the standard operational requirements of server such as Linux and Windows server on the guest server machines. This virtualization administrators use this platform to deploy, host and manage virtual machines. This platform also distributes the hardware resources like CPU, networking, memory and storage to virtual machines. The monitoring component of this platform manages the distribution & allocation of the computing resources of the physical server among the virtual machines and controls their performance and use.
VMWare (VMWare hypervisor)
VMWare is a multi-tenant environment through which a single hardware is distributed among different virtual machines. The server of VMware works using Solaris, Windows, Netware and Linux, all or any of that can be used simultaneously on the identical hardware. A virtual server could be built one time and can be deployed more than one time in the diverse environments with VMware server. The software testing can be done easily without setup in virtual machines with VMware server. The operations of legacy operating systems and software can be conducted in virtual machines which take the advantage of advanced infrastructures [42]. VMware also allows controlling the access to the virtual machines by configuring the permissions to meet the users’ needs. The selected virtual machines can be initiated automatically when VMware Server starts (Figure 6). VMware Support is provided for Windows Server 2008, Windows Vista, Linux 5, Red Hat Enterprise and Ubuntu 7.10 in 32 & 64 bit versions (Table 4).
Figure 6: Native and Containerized Applications.
Table 4: A comparison between Xen, KVM, Virtual Box and VMWare.
Libvert KVM (Linux hypervisor)
A complete virtualization option for Linux on the x86 hardware comprising virtualization extensions (Intel VT or even AMD-V) is KVM (such as Kernel-based Virtual Machine). KVM is made up of loadable kernel module, kvm.ko that offers the center virtualization infrastructure along with a chip specific module, KVM -Intel. With KVM several virtual machines can be deployed including unmodified Linux or even Windows images. Each virtual machine includes personal shredding hardware: disc, graphics adapter, a community card etc. KVM is an open source program. The kernel part of KVM is contained in mainline Linux, also of 2.6.20. The userspace part of KVM is contained in mainline QEMU and additionally Android 2.2 and GNU/Hurd [20]. Solaris 10 U3 along with Darwin 8.0.1, jointly with additional operating systems along with a few newer versions of these recorded, are proven to operate with specific constraints. By itself, KVM doesn’t carry out any emulation. Instead, it displays the dev/kvm port. Setup the guest VM’s address area. The firmware image must also be provided by server (normally personalized BIOS when emulating PC’s) the guest may use to bootstrap to its principal OS.
Cloud Service Providers
Cloud computing components are offered by cloud service providers typically SaaS (software as a service), IaaS (infrastructure as a service), or PaaS (platform as a service) to businesses & individuals. Customers can purchase increasing variety of services from cloud service providers. Cloud providers are also categorized [43,44] by whether they deliver public cloud, hybrid cloud or private cloud services.
Amazon AWS
AWS is the largest and most secure system of cloud computing [45] environment and a wide variety of infrastructure services are supported by it such as computing power, networking and database storage etc. The static websites can be hosted by users by using the AWS services. The users can develop the complicated solutions by employing AWS solutions which are flexible, scalable and reliable.
Google cloud platform
Hard disks and virtual machines tools located in the Google data centers are utilized by Google Cloud Platform [46]. It is an integrated storage system utilized by enterprises and programmers Google Cloud Platform is an integrated storage system utilized by programmers and enterprises to get the live data.
Microsoft azure
It can be employed for managing, deploying & designing the software through the worldwide network. Microsoft Azure was formerly called Windows Azure. Microsoft Azure service provider supports different databases, frameworks, operating systems, databases, programming languages and frameworks etc. [47].
Rackspace cloud
Different services of cloud computing are provided by Rackspace Cloud such as web application hosting, Cloud Files, Cloud Block Storage, Databases, Cloud files, Cloud Servers and Cloud backup etc. The block storage of Rackspace Cloud [48] employs a composition of solid state and hard drives in order to provide high performance. The backup of Rackspace Cloud [49] utilizes encryption & compression methods & the backup files are provided with reduced price. The users of services of Rackspace Cloud are billed according to their use.
IBM
Utilizing IBM Cloud an enterprise can have the freedom to select cloud tools, information units and delivery units for designing/ creating next-generation applications or services [13]. IBM Cloud can be utilized to construct pioneering way outs and can give businesses and companies more value. Using IBM Bluemix Cloud platform, high performing services and cloud communications in the IT environment can be integrated.
Verizon cloud
This Cloud platform has been built for maintaining workloads of business with high security and trustworthy performance [44]. One can choose flexible and secure services for the enterprise with Verizon cloud. And it can also make data in the personalized environments more secure. Verizon cloud has low associated risks and can retain the integrity of data across different applications.
Open Source Virtualization Platform for Private Cloud
Private clouds [50,51] can be deployed using Cloud Computing software. There are several software stacks available to deploy private Clouds. We will discuss some of these here.
OpenStack (VM orchestration)
OpenStack is a set of software tools for building and managing the public & private platforms of cloud computing. This open source software is backed by some biggest hosting and software development companies and by other members of community. It is managed by OpenStack foundation and is considered to be the future of cloud computing. Many different components make up OpenStack and additional components can be added to fit the needs of the users because of the open nature of OpenStack. There are 9 core key components; The primary engine of computing is Nova, The objects and files storage system is Swift, The component of block storage is Cinder, The networking capabilities for OpenStack are provided by Neutron, The dashboard is called horizon, The identity services are provided by Keystone, The image services are provided by Glance, The telemetry services are provided by Ceilometer and Heat is the orchestration component. OpenStack is particularly suited for building software-as-a-service applications, either improvements upon existing solutions or new deployments. It can be used to deliver low cost, scalable and easy to manage storage. OpenStack is based on KVM hypervisors and can help businesses save licensing fees and provides agility within the infrastructure.
CloudStack
Open-source cloud computing platform for providing IaaS (Infrastructure-as-a-Service) environments is apache CloudStack. CloudStack has been designed to support managed service providers and business IT departments produce and run public cloud, personal cloud or even hybrid vehicles with capacities equal to Amazon’s Elastic Compute Cloud (Amazon EC2).
Eucalyptus
Eucalyptus is an open source application program for executing (IaaS) at a personal or hybrid computing environment. The Eucalyptus cloud system pools together virtualized infrastructure to make cloud tools for infrastructure for a support, system for a support along with storage for support. The title Eucalyptus stands for Elastic Utility Computing Architecture to Linking Your Apps into Useful Systems. Eucalyptus is compatible with Amazon Web Services (AWS) & Straightforward Storage Service (S3). It works with numerous hypervisors such as VMware, Xen along with KVM. It could be set up and set up by source code or DEB along with RPM packs. Internal procedures communications are procured via SOAP along with WS-Security.
OpenNebula
OpenNebula is an easy yet strong and adaptive turnkey open source way to construct private clouds and handle data center virtualization. OpenNebula’s maturity depends upon above a decade old application releases and thousands of venture deployments, being extensively used by research and industry leaders. OpenNebula is powerful, smart, simple and flexible.
VMWare vSphere
VMWare vSphere can also be used to deploy a private Cloud computing system. VMware workstation can be used to deploy a small-scale private cloud. VMware solution has been discussed in section 8.
Cloud Security
The risks and issues associated with cloud security in cloud computing are not well recognized even today [52] and are great barriers for adoption of cloud computing services. The cloud computing uses internet to deliver services hence cloud inherits the vulnerabilities of computer networks and internet as well as the weaknesses of virtualization. An IaaS model which is unsecured is susceptible to MITM, DDOS, Port Scanning and IP Spoofing network related security threats. Most of the security risks associated with cloud computing are related to data security. Most of the issues whether related to data visibility, data control or data theft are associated with shared data of customers on the cloud platform. The security issues of SaaS applications are generally centered on data and access. It is responsibility of every organization to understand what data is being shared in the cloud and who accesses the data and what level of protection they and CSP have applied. Protecting the data in IaaS is critical. As customer responsibility extends to network traffic, applications and operating systems, additional security threats get introduced. When cloud infrastructure is built, it should be determined that who can enter data in the cloud, the resource modifications should be tracked to identify the abnormal behaviors, orchestration tools should be secured and network analysis of both east-west and north-south traffic as a potential signal of protecting cloud infrastructure deployments should be added. The security threats are out of scope of this paper and a more detailed discussion on Cloud Security is [3]. Some of the important security threats are discussed in subsequent section. Figure 7 shows the complete classification of security threats faced to cloud computing.
Figure 7: VMWare Hypervisor.
DOS attack
DOS is a threat or malicious activity affecting the network available to users. The impact is very vast on infrastructures shared among trillion of users due to large coverage. It is more evident than single tenant architecture because of millions of users. The increasing uses of cloud services and virtualized data centers have opened up new weaknesses in Cloud Computing [53]. Like the modernity and innovation in technology these attacks are also modernized, and full infrastructure does not need to be hacked or attacked by the attackers. Botnets are really helpful in such attacks, they spread DoS quite quickly. The applications with low bandwidths and more resources are vulnerable to attacks more e.g. Twitter attack of 2009.
Abuse of resources
Poorly bonded cloud support deployments, completely free trials of cloud support, and deceptive accounts sign ups through payment ports make the cloud computing versions vulnerable to malicious attacks. The misuse cases of tools of cloud computing include things like EDoS or DDoS strikes, malicious attempts and e-mail spam.
Virtualization threats
Virtualization and cloud security have become serious issues of concern [54]. Virtualization is the latest trend that is used in public or private cloud or infrastructure to reduce the cost of physical machines. Virtualization makes it possible to run more than one operating system called virtual machines. Cloud can face various threats due to Virtual machines such as cross VM attacks, VM migration attacks, stepping stone attacks, VM escape and VM isolation attack.
VM escape
In this attack, the attacker runs the code on a VM that breaks out the operating system running within the VM allowing the direct interaction of attacker with hypervisor. Such attack gives the attacker access all VMs running on that particular host and the host operating system [55].
VM isolation attack
The virtual machines which run on the same physical hardware should be separated from one another. Though logical isolation exists between distinct VMS, the accessibility to same bodily resources may result in the data violation and cross-VM strikes. Isolation isn’t just required on storage apparatus, but computational and memory hardware needs good grained isolation of VMs.
Hypervisor issues and VM hopping
The software layer that manages the VMs and allows the VMs to run simultaneously is called Hypervisor. This coordinates the access to resources as well as hosting and managing virtual machines. The guest operating systems are run by hypervisor which is installed on server hardware. A few vulnerabilities of scheduler [44] may result in resource stealing or theft-of-service. The attacker on one virtual machine can gain access to the other virtual machine with VM hopping. The resource usage of the victim virtual machine can be monitored by the attacker. The attacker can alter configurations, delete the stored data and can endanger the VM’s availability, confidentiality and integrity (Figure 8). The prerequisite for the VM hopping attack to take place is that the two VMs are running on one same host, and the IP address of the targeted VM is known by the attacker.
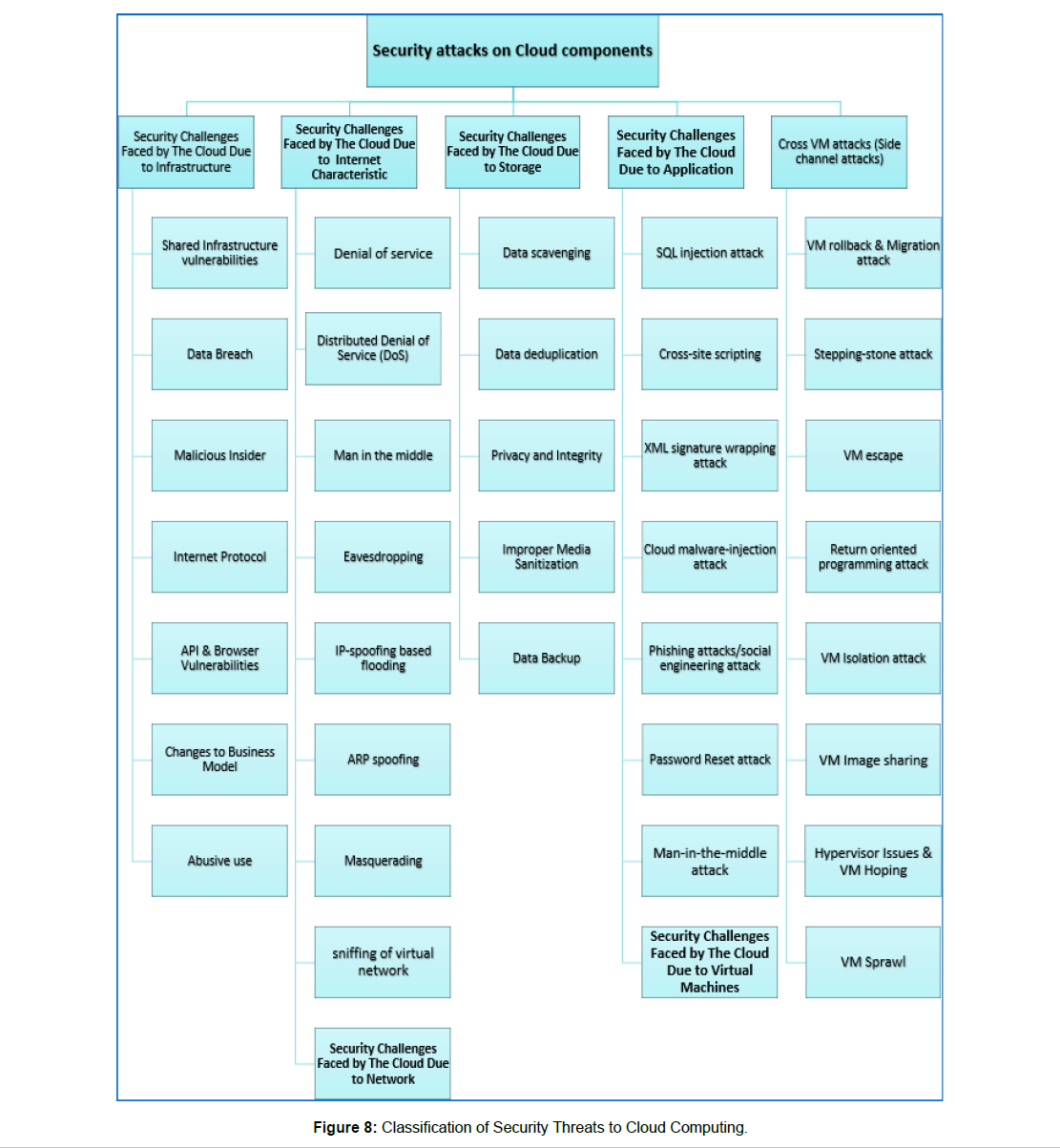
Figure 8: Classification of Security Threats to Cloud Computing.
Phishing attack
Phishing attacks also known as social engineering attacks are conducted by sending malware emails that direct the users to spoofed sites. These attacks are harmful for enterprise as well as user. Attackers manipulate the users to access confidential information.
SQL injection attack
The most common threat is the SQL injection attack. A malicious code is injected in this attack and the user’s information is stolen. When data is passed by user, attacker inserts personalized characters in it. It will change the nature of information and query. Resultantly the access to database can be gained by attackers and they become able to run their SQL injection commands against database and can alter, delete, and break the standard database design.
Data scavenging
The attackers can recover the deleted data in cloud environment through different ways. Data cannot be completely deleted unless the device is destroyed. The collection of information from recovered data is known as data scavenging. Data scavenging may allow attacker to recover sensitive data.
Multi-tenancy
Multi tenancy means sharing of resources among multiple cloud users. These users among which resources are shared are called tenants [56]. It simply means a single cloud platform between various users. The virtual platform allows multiple running like JVM and .NET. Co-tenancy and co-location attacks can destroy multi tenancy. DoS attacks and illegal accessing of neighbor VMs is another big threat.
Malicious insiders
This is considered a most dangerous threat which is difficult to mitigate with the use of software and instead strict policy enforcement is the only sure way to minimize malicious insider an attack. An insider hazard can take unique types such as a system administrator, former worker, business spouse or a third-party contractor. A threat could be catastrophic. For example, a British breach in Sage, led to the dropping the inventory cost of organization by 4.3 percent, causing tens of thousands of dollars in reductions. The security of systems which depend on the cloud service providers solely is at greater risk. The potentially private info of the users can be accessed by malicious insider [57] such as a system administrator and they can obtain increasing amounts of accessibility to more crucial methods and can cause breach of information.
Recent Technology Trends Enhancing Cloud Computing Landscape
Following are some of the tools that are changing the cloud computing landscape.
Software defined networking
SDN [58] is a new trend in which the data plane and the control plane are separated for networking devices for efficiency. An SDN controller [59,60] is a program in a software-defined network (SDN) structure that handles flow management for enhanced network management and program functionality. The SDN control platform generally runs on a machine and utilizes protocols to inform buttons where to send programs. There are various SDN controllers available such as ODL, Cisco ACI, and Juniper Contrail. Here we will discuss two of the open source SDN controllers
Open daylight controller
Open Daylight is modular open platform for automating and customizing networks of any scale and size. The ODL provides a framework to migrate from existing network to SDN architecture [18]. It has been deployed in enterprises, data centers, carrier networks and supports a wide range of use cases. Open Daylight provides programmability, abstraction and openness that defines a way towards intelligent software defined infrastructure. SDN is emerging rapidly as dynamic architecture of networking to address NFV and cloud networking demands [61]. The open source platform is the enabler for motivating vendors and operators to collaborate and benefit from this innovation over long term.
ONOS – Carrier grade SDN operating system
Linux foundation hosts an open source community called open networking operating system (ONOS) which is designed to help the network service providers in building carrier grade software defined networks for high availability, scalability and performance [62]. Both ODL and ONOS have modular designs and have a similar goal of advancing SDN [63]. The two projects, however, have different approaches and have different partners and backers. The focus of ONOS is primarily service provider networks while the focus of ODL is data center networks [44]. Also, ONOS is designed to provide better network performance which the purpose of designing ODL is merging legacy networks to SDN.
SDN orchestration
SDN orchestration is the ability to program the automated behaviors in network. The SDN orchestration is responsible for coordinating the networking software and hardware elements which support the applications and services. Its most important element is the ability to automate connectivity and monitor the network. SDN orchestration is the promising area of growth of SDN based networks. SDN orchestration is expected to provide important binding force of broad range of technologies which enable network services and cloud-based communications. It is also expected that it will provide coordination and automation technology that will ultimately bridge the gap between OSS systems, telecom systems, data center resources and the customers looking to purchase the cloud-based network and technology services.
OpenFlow (switching/routing protocol) enabling SDN controllers
An OpenFlow Controller utilizes the OpenFlow Protocol. An SDN Controller would be the tactical stage in software-defined system (SDN). An OpenFlow Controller [64,65] employs the OpenFlow protocol to attach and configure the network devices (switches, routers, etc.) to automatically ascertain the ideal path for traffic. SDN Functions may simplify system management, managing all communications between devices and applications to efficiently handle and alter network demands. An OpenFlow based SDN Controller supplies data to the switches/router through southbound APIs as well as the software and business logic through northbound APIs.
IoT (Internet of things)
The IoT is a method of interrelated computing apparatus, electronic and mechanical machines, things, creatures or individuals which are supplied with the specific identifiers (UIDs) along with the capacity to transport information within a network without needing human to computer or human-to-human interaction. This item could be an individual who has heart monitor transplant, farm animal using biochip transponder, or a car that has built-in detectors to keep the driver alert when the pressure of tire is reduced or some other man made or natural thing to which an IP address can be assigned and can transfer information within a network. An IoT eco-system is made of web-enabled smart devices which use embedded chips, sensors and communicating hardware to get, send and behave on data they acquire from their surroundings.
Blockchains
The financial transactions’ incorruptible digital ledger is a Blockchain which can be programmed to document not simply monetary transactions but practically all worth [66]. There are two varieties of blockchain implementations: ‘’trustless’ and ‘trusted’. A trustless case is a Bitcoin, in which the block chain database is not saved in any specific place, meaning that the documents it keeps are really public and readily digestible. No centralized variant of the information is different for a user to corrupt. It’s hosted by countless computers concurrently, and its information is available to anybody online. It’s effectively an electronic contemporary variant of a conventional ledger run by means of a financial institution. A trustworthy illustration is that the financial authority of Singapore (MAS) strategy to trial blocks chain for a technique to repay interbank transfers. The execution utilizes the very same technology and procedures as the trustees established program, but it run on a personal system and the ledger systems are efficiently computers inside that personal network. Blockchain technologies, nevertheless, is not just confined to cryptocurrencies such as Bitcoin. Its cryptographic way of spreading data and documenting trades lends itself into a nearly infinite variety of programs, from property titles such as loans, transactions, intellectual property, and identification confirmation, along with other matters.
Cloud Computing Challenges
Cloud Computing faces several challenges [67] that can affect its growth and usage. Cloud Computing has some open research problems such as Availability of Service, Data Confidentiality, Data Lock-in, [68] Transfer Bottlenecks, Unpredictable Performance, Bugs in distributed systems, Invention of Scalable Storage, Quick Scaling, etc. These challenges are discussed in detailed in this survey papers. We will discuss a few other challenges which are not discussed in much detail in these survey papers.
Availability of services
Availability, performance and security are major areas of concern for consumers in cloud computing. The availability is the uptime of system, hardware, network of systems or software that provides the service collectively. While cost effective solutions are provided to the consumers and businesses by cloud computing; the cloud service providers should also provide highly available environments. Technically high availability can be achieved at several levels. These levels include infrastructure level, data center level, geographic location level and application level. The basic goal to provide highly available environments is to avoid single points of failures in order to achieve failover capability, operational continuity and redundancy.
Vendor and data lock-in
Vendor lock-in is one of the potential drawbacks in cloud computing. Vendor lock-in is the situation in cloud computing in which the customers become dependent on technology implementation, services and products of a single cloud provider and cannot move easily to different vendor in future without legal constraints, substantial costs or technical incompatibilities. For Example, an Internet storage service ‘Linkup’ shut down its service which depended on Internet storage supports Nirvana to store client Info because of changes in the agreement and inability to move client data.
Security challenges
Cloud security has been discussed in a previous section but for the completeness we will briefly discuss this as security is among the prior most challenges in cloud computing. In previous years we watched many cyber-attacks ever recorded in the history of the World Wide Web. Many experts forecast coming years will see greater personal and state-sponsored strikes targeted at sabotaging cloud infrastructure safety. Cyber-attacks are also getting more sophisticated, so anybody responsible for the company’s safety will have to be complicated in the manner in which that they detect and avoid such attacks. Cloud providers are going to have the ability to assist businesses with their safety measures by providing managed services.
Data confidentiality
The maintenance of the confidentiality of data in cloud environment is a primary issue. The data which is sent to cloud is not stored in a single storage server of cloud. It is replicated to different data centers of cloud. Data centers are maintained and controlled by different CSP experts [69]. The cloud data is susceptible to different kinds of threats. The security of data is even more complicated in cloud computing than security of data in traditional information systems. In order to make the cloud computing more common among enterprises and users, the concerns of the users regarding the security of cloud computing should be rectified in order to make the environment of cloud computing trustworthy.
Data transfer bottlenecks
In cloud computing, bottleneck is a point where the flow of the data is impaired or stopped entirely in the enterprise. Data transfer bottleneck can occur in user network, storage fabric or within the servers where there is a contention for the resources of server such as memory, I/O, CPU processing power. As a result of this, the data flow slows down very much. This slow down speed affects the performance of the application especially for heavy applications and databases and it can even cause the applications to crash in some cases.
Unpredictable performance
Performance predictability is an important challenge in cloud computing data center and particularly in IaaS (Infrastructure as a service). For an allocated VM (virtual machine) in IaaS, the client expects his application to perform in an identical manner whatever is the resource management strategy or hosting physical server. However, in heterogeneous hardware environment (i.e. where machines don’t have same performance characteristics), it becomes difficult to enforce performance predictability and it becomes even more difficult when the machines are heterogeneous internally.
Invention of scalable storage
In cloud computing Scalability is a challenging task to effectively utilize the resources. In the recent years, enterprises and companies have made efforts to achieve application, platform, and infrastructure level and database scalability. The advantages of scaling come with set of complexities. While on demand scaling is possible in cloud computing, applications too need to be able to scale with the environment. This may look simple, but there are considerations that need to be made while opting for scaling session information, data and uploads.
Bugs in distributed systems
Unlike the systems with single server, the cloud systems are considerably complex as they deal with a range of distributed components, users, hardware failures and deployment scenarios. Cloud systems can periodically experience the downtimes. In the distributed systems, there might be a few lines of code but there can be quite long trail of dependencies. The bugs can move anywhere in distributed system due to the chain of dependencies.
Software licensing
In cloud computing the licensing of the software should be made simpler. However, in some cases software licensing can get worse. Although some vendors of software are innovating software licensing and are offer customers a ‘pay as you go’ model, some others still do not have defined policies to make the software cloud friendly. To determine the appropriate software licensing, consumers need to understand the hardware architecture, look into the vendor tables and then need to do a great number of calculations to get correct sizing for the software product.
Cloud interoperability
Cloud interoperability is switching from one environment to another, for example from private cloud to public. IEEE and ISO specify interoperability as the capability of a couple of software’s or systems to exchange the data [70] and use the information that has been exchanged. In the context of cloud computing systems, interoperability should be viewed because the capacity of cloud solutions, personal cloud solutions, along with other varied systems within the business to understand one another’s cloud platform and support ports, configuration, kinds of authorization and authentication and data formats etc. to be able to operate with one another.
It’s important to realize there are different Areas of interoperability that could be described as different facets.
Cloud standards
Cloud standards are the set of rules and measures that tend to tackle the practices of cloud computing ethically. Cloud computing has gained popularity in the recent years. Industry observers say that cloud computing still lacks comprehensive standards despite of many groups working on them. The lack of standards can make the use of cloud computing trickier. It can also restrict implementation by limiting the interoperability.
Data mining in cloud computing
The technique of data mining is used for extracting the useful information from raw data. In cloud computing, data mining allows the organizations to centralize the management of software and data storage, and assures efficient, secure and reliable services for their users. The cloud computing refers to hardware and software delivered as services over the internet, the software of data mining is also provided in this way. Using data mining services through cloud computing reduces the barriers that keep small companies from benefiting from the services of data mining [71]. The data mining techniques’ implementation through cloud computing allow the users to retrieve meaningful information through virtual data warehouse which reduces the costs of storage and infrastructure. From the perspective of data mining, it has opened many new opportunities and challenges in cloud computing paradigm. The existing data mining techniques encounters great difficulties when required to handle the volume, unprecedented heterogeneity, speed, accuracy and privacy of data.
Laws, Policies and Regulations Governing Cloud Environment
Cloud computing environment is regulated by laws and policies. There are federal, state and even international laws which impose certain responsibilities on the providers of cloud computing as well as tenants. These laws and policies regulate the way the data is collected, stored and processed. Some of these laws and regulations used in United States and Europe are discussed below:
HIPAA (Health Insurance Portability and Accountability Act):
The Privacy Act of HIPAA regulates the use of protected health information. The protected information cannot be disclosed or used in cloud environment unless as required or permitted by the rule. HIPAA deals particularly with EPHI (Electronic Protected Health Information). The rule identifies various security standards regarding the use of patients’ data. The department of human services and health OCR (office of civil rights) recently issued guidance on cloud computing and HIPAA that confirms that CSPs are business associates under the HIPAA act.
The Gramm-Leach-Bliley Act (GLBA):
This Act imposes regulates privacy implications on financial institutions for storing data in cloud and consists of two principles ‘safeguards rule’ and ‘financial privacy rule’. The financial privacy rule governs the collection and disclosure of customers’ personal information by the financial institutions. According to the rule of financial privacy, financial institutions must provide customers with privacy notice which explains how the financial information of users is being shared, used, collected & protected. The safeguards rule requires the financial institutions to develop, maintain and implement the comprehensive program of security to protect the nonpublic information of customer. The safeguards rule also requires the financial institutions to monitor and test their security programs periodically.
The electronic communications privacy Act of 1986 [26]
The electronic communication Privacy Act (ECPA) protects the use, access, disclosure, privacy and interception of electronic communications. The service providers are prohibited from divulging communication contents when the contents are in the electronic storage by ECPA. The law also prevents the entities of government from disclosing electronic communications like email messages without the proper procedures (i.e. warrant).
State specific regulation
Keeping the data private and secure in a cloud environment is not so easy. The laws and regulations for data privacy and security differ from country to country. European Union is the largest economy in the world and is concerned about its competitiveness in the digital world. It has proactively pursued policies to promote legal certainty. U.S has also developed a framework of regulations and laws for privacy protection in different circumstances. While the majority of cloud regulations and technologies have origins in United States and Europe, other regions are also playing important roles in development of digital privacy protection.
General data protection regulation (GDPR)
The GDPR (general data protection regulation) strengthens the personal data protection in Europe and impacts the ways in which businesses are done. On May 25, 2018, GDPR came into effect and replaced the 1995 EU data protection directive. The GDPR regulates the ways in which businesses can use, collect and store personal data. It also authorizes fines on the businesses which fail to meet its requirements.
Upcoming Cloud Computing Technologies
Future of cloud computing is very eventful [23]. Following are some of the major changes expected to happen in future of cloud computing
Storage capacity
A massive aspect impacting the cloud computing potential is the quantity of storage cloud computing systems provides companies and people. This expansion is due to the fact that companies are embracing cloud technologies as a massive portion of conducting business. It’s predicted that hardware providers will continue to deliver at an accelerated rate more data centers on the internet with larger-capacity storage gear for the next decade. With this higher storage, more companies are going to have the ability to store massive data collections and perform advanced analytics utilizing computing. Being able to perform analytics on this huge amount of data enables companies to gain invaluable insights into client behavior, individual systems, and tactical financial investments.
Internet of everything (IoE)
IoE brings people, procedure, information, and items to earn networked relationships more applicable and more beneficial than ever before. It constitutes turning data into activities that produce new capacities, richer experiences, and unparalleled financial chance for companies, people, and nations.
Quantum computing
Instead of storing data using pieces represented by 1s or 0s as traditional electronic computers perform, quantum bits are used by quantum computers, or qubits, to encode data such as 1s, 0s, or even both at precisely the exact same moment. This superposition of the states and all the other quantum mechanical phenomena of tunneling and entanglement empower quantum computers to control monumental combinations of states simultaneously.
Neural networks based cloud computing provisioning
Machine learning approach is the ability of the system to automatically learn and improve experience regardless of the need to explicitly being programmed. Resource provisioning is a challenging task in cloud environment due to the need of dynamic provisioning of resources to applications. In the environment of cloud [72], resources allocation to the application is expected to be dynamic according to the workload pattern of application. Variations in the resource provisioning can lead to wastage of energy and cost and can also cause dropping in Quality of Service (QoS) and the violations of Service Level Agreements hence the resource allocated to the application should be close to the current workload of the application. The determination of the future demands of resources to application is a crucial step before allocation of resources in a cloud environment [73]. Thus, the prediction of the resources required to the application like number of physical machines and virtual machines, number of requests and workload etc. is a step of great importance. Based on the techniques of machine learning and prediction results, enough amount of resources can be allocated to applications in right time and the QoS dropping and SLA violation can be avoided. Neural networks are set of algorithms that have brought revolution in machine learning. The current deep neural networks have proven to work well and are inspired by the biological neural networks. Neural networks are general function approximations that can be applied to any problem of machine learning about learning a complex mapping from input to output space. The next generation of cloud computing provisioning for large environments will be based solely on Neural Networks.
Hybrid cloud solutions
A hybrid is a computing environment which unites a community cloud along with a personal cloud by letting applications and data to be shared between them. It provides the capability to easily scale on-premises infrastructure around the people cloud to deal with any overflow. Organizations benefit the flexibility and computing ability of their general cloud for fundamental and non-sensitive computing jobs, while retaining business-critical data and applications onpremises, securely behind a business firewall.
Server-less cloud computing
Server less cloud computing is a new emerging phenomenon where there is no use of cloud servers for any purpose like storage and computation. Rather than server allocation is done automatically. It makes the cloud simpler and easier to use.
G Networks
5G Networks is the future telecommunication technology profoundly dependent on cloud computing or simple mobile cloud computing. It offers fastest network speedy and provides reliable connectivity. These connections are going to be multi times faster than normal connections. This will power the structure of Internet of Things Technology. With 5G world will be connected in smarter ways.
Containers, Kubernetes in cloud computing
Containers and Kubernetes will continue to have an impact on the Cloud Computing future. Kubernetes is a mobile, flexible opensource platform for handling containerized workloads and solutions that eases both declarative automation and configuration. It’s a large, fast growing ecosystem. Kubernetes providers, service, and resources are frequently available. Kubernetes supplies a container-centric direction atmosphere. This provides a lot of the ease of Platform for a Support (PaaS) together with the flexibility of management for a Support (IaaS) and empowers reliability across infrastructure suppliers.
Mobile cloud computing
MCC systems [4] are a model or technique where cellular applications are constructed, hosted and powered with cloud computing technologies. A cellphone cloud system allows developers to construct applications designed especially for mobile users with no memory or computing capability of this smartphone. Mobile cloud computing systems based are usually obtained with a mobile browser by a distant web server, generally without necessity for installing new client program on the receiver phone.
Fog computing
Fog computing [71,74], also referred to as fog network or fogging, is a decentralized infrastructure of computing where information, storage & software are distributed in the most efficient, logical location between the information source and the Cloud. Fog computing extends cloud computing solutions to the border of the community, bringing the benefits and power of this cloud nearer to where information is generated and acted upon. It increases efficiency.
Edge computing
Edge identifies the computing infrastructure which exists near the sources of information, for example, industrial computers (e.g. magnetic resonance scanner, wind turbines, undersea blowout preventers), the industrial controls like SCADA systems, and time series databases aggregating data from many different equipment and detectors. These advantageous computing devices live away in the centralize computing accessible in cloud environment.
Future Work
We are using machine learning and Neural Networks discussed in this survey paper to mitigate security & performance issues in cloud computing environment when these networks at a massive scale. We are in the design and implementation phase to study ML analytical engines to process large amount of data collected in the cloud and deploy a test bed of OpenStack and Open Daylight controller and test the planned machine learning model.
Conclusion
This survey reviews the current landscape of Cloud environment and discussed Cloud Computing models, services, challenges, policies, regulations and future of cloud computing. The significant way cloud is currently dominating the IT marketplace, it can be anticipated that this growth will continue for the next years with many new use cases and technologies shaping it. We have discussed technologies such as containers, Kubernetes, OpenStack, Software Defined Networking and Machine Learning. We presented in this paper how Cloud computing provides competitive advantage to enterprises in the current market with reduced IT cost, the ability to free up staff for managing IT infrastructure responsibilities and better service providence to customers by offering IAAS, PAAS and SAAS. We have highlighted in the paper that Cloud Service Provider space will continue to grow and more CSPs will emerge offering scalable, efficient services with lower pricing. We also discussed that mobile cloud computing system is predicted to emerge as among the largest market for cloud providers and cloud programmers. The cloud computing is triggering a serious impact on many fields such as data mining and big data. Although cloud computing has the potential to change the way computing is done, it still faces some challenges like data lock-in, data confidentiality, transfer bottlenecks, scaling, bugs in distributed networks etc. which have been discussed in this paper. An insight into cloud security vulnerabilities have also been presented in this paper. Cloud computing is still at nascent stage of development and there is still much potential in this era which can be realized owing to ongoing development and research in this field.
Conflict of Interest
Wajid Hassan declares that he has no conflict of interest.
References
- Fang L, Jian T, Jian M, Robert B, John M, et al. (2011) NIST Cloud Computing Architecture.
- Peter M, Grace T (2011) The NIST Definition of Cloud Computing.
- Hassan W (2019) Latest trends, challenges and Solutions in Security in the era of Cloud Computing and Software Defined Networks.
- Gayathri MR, Srinivas K (2014) A Survey on Mobile Cloud Computing Architecture, Applications and Challenges. Int J Sci Res Eng Tech 3.
- Dinh HT, Chonho Lee, Dusit Niyato, Ping Wang (2011) A survey of mobile cloud computing: architecture, applications, and approaches. Wirel Commun Mob Comput 13: 1587-1611
- Patrícia TE, Glauco EG, Judith K, Djamel S (2008) A Survey on Open-source Cloud Computing Solutions.
- Subashini S, Kavitha V (2011) A survey on security issues in service delivery models of cloud computing. J Net Comp App 34: 1-11.
- Bhaskar P, Eunmi, Ian Lumb (2009) A Taxonomy and Survey of Cloud Computing Systems. Fifth International Joint Conference on INC, IMS and IDC 44-51.
- Ajay M (2015) ACM Tech Pack on Cloud Computing.
- Mohsin N (2012) Cloud Computing: Overview & Current Research Challenges,” IOSR Journal of Computer Engineering (IOSR-JCE) 8: 14-22.
- Niroshinie F, Seng WL, Wenny R (2013) Mobile cloud computing: A survey. Future Generation Computer Systems 29: 84-106.
- Palvinder S, Anurag J (2014) Survey Paper on Cloud Computing. International Journal of Innovations in Engineering and Technology (IJIET) 3: 84-89.
- Kalpana T, Sachin C, Kumar S (2015) Survey Paper on Cloud Computing. International Conference on Emerging Trends in Technology, Science and Upcoming Research in Computer Science.
- Shancang Li, Li Da Xu, Shanshan Z (2018) 5G Internet of Things: A Survey. Journal of Industrial Information Integration 10:1-9.
- Rajkumar S (2018) A Manifesto for Future Generation Cloud Computing: Research Directions for the next Decade. ACM Computing Surveys 51.
- Jasenka F (2018) Survey of Communication Protocols for Internet-of-Things and Related Challenges of Fog and Cloud Computing Integration. ACM Computing Surveys 1.
- Wei Yu, Liang F, Xiaofei H, William GH, Chao L, et al. (2017) A Survey on the Edge Computing for Internet of Things. Mobile Edge Computing 6: 6900-6919.
- Buyya R, Son J (2018) Software-Defined Multi-Cloud Computing: A visuion, Architectural Elements and Future Direction.
- Bowen Z, Rajkumar B (2018) Augmentation Techniques for Mobile Cloud Computing: A Taxonomy, Survey and Future Directions. ACM Comput Surv 51.
- Steingier M (2018) Factors influencing the organizational adoption of cloud computing: a survey among cloud workers. International Journal of Information Systems and Project Management 6: 5-23.
- Babur H, Faisal M, Sohail S (2018) From cloud computing to fog computing in Hahealthcare Big Data. MATEC Web Conf 189.
- Jianli P (2017) Future Edge Cloud and Edge Computing for Internet of Things Applications. IEEE Internet of Things Journal 5: 439-449.
- Varghese B, Rajkumar B (2017) Next Generation Cloud Computing: New Trends and research Directions. Future Generation Computer Systems 79: 849-861.
- Shanhe Y, Zhengrui Q, Qun L (2015) Security and Privacy Issues of Fog Computing: A Survey.
- Likitha G, Murali K (2018) Survey of Cloud Computing and its Application. International Journal Advances in Scientific Research and Engineering 4: 23-26.
- Meetu K, Kalyani P (2018) Survey of Machine Learning Algorithms for Dynamic Resource Pricing in Cloud. International Journal of Scientific Research in Science, Engineering and Technology 4: 93-97.
- Ranjith KC (2018) Survey on Cloud Computing Services and Challenges. International Journal of Computer Sciences and Engineering 6.
- Anthony T (2010) Cloud Computing: A Practical Approach.
- A Guide to getting started with Cloud Computing. Sun Microsystems (2014).
- Buyya R, Vecchiola C, Thamarai Selvi S (2013) Mastering Cloud Computing Foundations and Fundamental Programming.
- Michael A (2010) A View of Cloud Computing. ACM 53: 50-58.
- Voorsluys W, Broberg J, Buyya R (2011) Introduction to Cloud Computing Services.
- Tak BC, Urgaonkar B, Sivasubramaniam A (2011) Understanding the Cost of Cloud: Cost analysis of In-house vs. Cloud-based Hosting Options.
- Tak BC, Urgaonkar B, Sivasubramaniam A (2011) To Move or Not to Move: The Economics of Cloud Computing.
- Mohammad I (2010) Cloud Computing and Software Services: Theory and Techniques.
- Hai J (2015) Towards Optimized Fine-Grained Pricing of IaaS Cloud Platform. IEEE Transactions on Cloud Computing 3: 436-448.
- Ali A (2007) S3: A Service-Oriented Reference Architecture. IT Professional 9: 10-17.
- Liang-Jie Z, Qun Z (2009) CCOA: Cloud Computing Open Architecture. IEEE International Conference on Web Services.
- Paul B (2003) Xen and the Art of Virtualization.
- Nakhate RT, Gandhi SG (2013) Survey Paper on Cloud Computing. International Journal of Scientific and Research Publications 3.
- David B (2014) Containers and Cloud: From LXC to Docker to Kubernetes 1: 81-84.
- Gabriel LS (2018) Running Mac OS X as a QEMU/KVM Guest.
- Coyne L (2018) IBM Public, Private and Hybrid Cloud Solutions.
- Kuyoro SO, Ibikunle F, Awodele O (2011) Cloud Computing Security Issues and Challenges. International Journal of Computer Networks (IJCN) 3: 247-255.
- Siegele L (2008) Let It Rise: A Special Report on Corporate IT. The Economist 389.
- Amburst M (2009) Above the Clouds: A Berkeley View of Cloud. Berkeley.
- Garfinkel S (2007) An Evaluation of Amazon’s Grid Computing Services, Harvard University.
- Sayah JY (2005) On-demand business collaboration enablement with web. Decision Support System 40: 107-127.
- Cloud Computing Use Case White Paper Version 4. Cloud Computing Use Case Discussion Group, (2010).
- Rajkumar B (2010) Cloud Computing Principles and Paradigms
- Endo PT, Gonçalves GE, Kelner J, Sadok D (2010) A Survey on Open-source Cloud Computing Solutions.
- Security Guidance for critical areas of focus in Cloud v4.0. Cloud Security Alliance, (2017).
- Josyula V, Orr M, Page G (2011) Cloud Computing: Automating the Virtualized Data Centre.
- Kumar V (2013) Survey Paper on Cloud Computing. International Journal of Engineering and Advanced Technology (IJEAT) 2: 2249-8958.
- Chou TS (2013) Security Threats on Cloud Computing Vulnerabilities. International Journal of Computer Science and Information Technology (IJCSIT) 5.
- Niranjan SJ, Gairish D (2016) The Survey Paper on Cloud Security using RBAC model, International Research Journal of Engineering and technology 5: 1182-1187.
- Bruce G (2015) Cloud security Certification.
- Hassan W (2018) Future Controller Design and Implementation Trends in Software Defined Networking. Journal of Communications 13: 209-217.
- Mehmet U, Jiang (2013) IEEE Software Defined Network Initiative.
- OpenStack, Orchestration, (2018).
- White R, Donohue D (2014) The art of network architecture. INpolis, IN:Cisco Press.
- López V, Gonzialez O, Fuetenes B, Lopez (2014) Towards a Network Operating System.
- Jungmin S, Rajkumar B (2018) A Taxonomic SDN Enabled Cloud Computing. ACM Computing Surveys 51.
- Nader B (2014) Network Virtualization and Cloud Computing. Microsoft System Center.
- McKeown N (2008) OpenFlow: Enabling innovation in campus networks. ACM SIGCOMM Computer Communication 38: 69-74.
- Tapscott, Don, Alex (2016) Blockchain revolution.
- Dillon T, Wu C, Elizabeth C (2010) Cloud Computing: Issues and Challenges. 24th IEEE International Conference on Advanced Information Networking and Applications.
- Furht B, Escalante A (2010) Handbook of Cloud Computing.
- John JP (2011) Prediction of Cloud Data Center Networks Loads Using Stochastic and Neural Models. In Proc. of the 2011 6th International Conference on System of Systems Engineering, USA.
- Zhang LJ (2010) Hot Topics in Cloud Computing.
- Wang Y (2015) Fog computing: Issues and challenges in security and forensics. In Computer Software and Applications Conference (COMPSAC).
- Jegadeeswari S, Dinadayalan P, Gnanambigai N (2016) Enhanced Data Security Using Neural Network in Cloud Environment. International Journal of Applied Engineering Research 11: 278-285.
- Rajkumar B, Gopikiran T, Satyanarayana S (2013) Neural Network Design in Cloud Computing. International Journal of Computer Trends and Technology 4: 63-68.
- Stojmenovic I (2015) An overview of fog computing and its security issues. Concurr Comput 28:2991-3005.
 Spanish
Spanish  Chinese
Chinese  Russian
Russian  German
German  French
French  Japanese
Japanese  Portuguese
Portuguese  Hindi
Hindi 