Research Article, J Comput Eng Inf Technol Vol: 11 Issue: 8
Determination of User Factor Requirements for Acceptable of Biometric Voter Registration Technology
Richard Kayanga Nyakundi1*, Samuel Mbuguah2, and Ratemo Makiya3
1Department of Computing and Informatics, Kibabii University, Bungoma, Kenya;
2Department of Computer Engineering, Kibabii University, Bungoma, Kenya;
3Department of Computing and Informatics, Kisii University, Kisii, Kenya
*Correspondence to: Richard Kayanga Nyakundi, Department of Computing and Informatics, Kibabii University, Bungoma, Kenya, Tel: 254720407540; E-mail: nyakundirich01@gmail.com
Received date: 04 April, 2022, Manuscript No. JCEIT-22-51831;
Editor assigned date: 06 April, 2022, PreQC No. JCEIT-22-51831 (PQ);
Reviewed date: 20 April, 2022, QC No. JCEIT-22-51831;
Revised date: 02 June, 2022, Manuscript No. JCEIT-22-51831 (R);
Published date: 14 June, 2022, DOI:10.4172/JCEIT.1000232.
Citation: Nyakundi RK, Mbuguah S, Makiya R (2022) Determination of User Factor Requirements for Acceptable of Biometric Voter Registration Technology. J Comput Eng Inf Technol 11:8.
Abstract
Voting systems around the world are transitioning from the manual voting practices to electronic systems for better service delivery. However, even with electronic systems, credibility of the technology has been a challenge to many countries around the world. This is because of electoral bodies focus on the technical supply-side factors with little emphasis on acceptable biometric technology systems. There has been inadequate research and development in IT models particularly leading to adoption and acceptance of BVR Technology to inform the publics’ uptake of acceptable election outcomes. While a number of adoption models have been and applied to the developed countries, they require domestication in order to address the specific client-based needs of developing nations. This study therefore was meant to establish the valid user factors that determine easy adoption and wide acceptability of the BVR technology. Analyzing the existing BVR technology and determination of usage factors for adoption of BVR Process formed the objectives of this study. Questionnaires and interview schedules were used as research instruments to collect data. Data was then arranged and coded for analysis. Descriptive statistics was used to analyze the collected data. Data presentation was done using tables and logical analysis. The study affirmed that paybacks, lack of reliance, negative exactitudes of technology users, inadequacy of government policy, lack of preparation in BVR technology and lack of edification in internet use led to low usage rate of BVR Technology.
Keywords: BVR technology; Consumer acceptance of BVR technology; User factors
Introduction
Despite the importance of implementing electronic technology processes, their implementation is still limited due to low adoption rates. The concept of biometric Voter Registration (VE) revolves around the adoption of a technology that the average voter must be aware of when designing systems to increase this number of voters. The biometric voter registration process is an initiative to improve voting systems as well as reduce costs and increase efficiency. Focusing on technical solutions alone changes the mindset of bureaucrats who are not involved in the decision-making process. The role of current biometric voter registration technology to bridge the gap between the proposed technology and biometric voter registration technology has not been underscored, and developing countries are far behind in implementation. To be effective, users need a model with inputs that lead to the use of the system best suited to their needs. Institutions generally do not involve voters in the development of biometric voter registration systems. In contrast, many internal programs focus on cost savings and other institutional guidance related to the effectiveness of voter registration. Studies of the acceptance of T are based on theories such as the Theory of Planned Behavior (TPB) and the Model of Technology Acceptance (TAM). Accept the use of people and information technology in your organization. A common feature of these paradigms is a personal belief or belief in a new technology that influences actual use behavior [1].
In particular, TAM models are designed to predict technology adoption and investigate user reactions to new applications. In particular, TAM predicts the Presumptive Income (PU) and the estimated utility (PEOU) two factors that affect the individual user behavior. PU refers to the situation in which an individual's performance is improved by using a particular system, and PEOU refers to the time it takes an individual to easily use a particular system. Beliefs influence the correctness of behavior, so behavioral intentions influence actual behavior when new technologies are used in organizations.Although the TAM model is widely used in the computer literature, it has also been criticized by researchers. It has been criticized for not adapting to the changing IT environment and ignoring the social impact of the IT implementation process. According to a study by Burton-Jones and Hubona, key TAM structures such as PU and PEOU are important predictors in attracting individual system users. However, he argues that both of these structures are imperfect predictors of system behavior and influence individual identities and habits [2]. They suggested that adoption and use of individual technologies could only be predicted by individual variables such as career, age, and brightness [3].
Previous knowledge about benefits as key indicators for acceptance was also questioned. TAMs are mainly developed and tested in culturally related industrialized countries and are often "accepted by the public on the basis of causal models". The briefly described relationship between cognition and behavior in African cultures may not follow this pattern [4]. Conversely, products with a high level of uncertainty, such as in South Africa and Africa, are usually under control and have fewer side effects, increasing awareness of the benefits and effectiveness of using them correctly. Availability of technology other positive perceptions of this technology. Ease of use has also been used as a measure of system quality in successful information systems research. In this regard, WWW studies were carried out in parallel and user friendliness was seen as part of the quality of the web system. A recent study found that perceived usability is an important part of measuring customer satisfaction with a website. Web technologies are designed in learning environments to make the learning process easier so the usability of a sound/necessity is endless, especially when students are unfamiliar with computer technology and the internet. One type that indirectly refers to ease of use was 1996.
An important external variable influences the perceived benefit as it does not have a significant impact on its use in developing countries. Some studies have understood the importance of usefulness and highlighted its importance in this area, and less attention has been paid to the study of exogenous variables in EJISDC (2002). However, a review of the literature provides important examples. Not only technical features seem to play an important role, but also the user experience in technology and the coordination of tasks and skills [5,6]. Organizational support, self-efficacy, computer anxiety and computer games also predict ease of use. Factors such as perceived pleasure and the ease with which technology is used intentionally over time also play a role. Agarwal and Prasad understand the importance of individual differences as practical indicators and explicitly point out previous experience, educational level and information technology as influencing factors in the role [7].
Related Studies
Biometric voter registration in Kenya
With the promulgation of the new constitution in 2010, the Independent Electoral and boundaries commission was formed in Kenya that is tasked to conduct and run elections in Kenya among other mandates. They have since developed a voting system which is partially electronic. Voter registration and voter identification is usually done electrically by preprogrammed kits. After successful identification the voter then casts his or her vote manually using ballot papers. At the end of the voting exercise the votes are counted and transmitted electronically to the main IEBC servers for further verification and announcement. This process aimed at solving vote tampering and rigging witnessed in earlier elections such as in 2007. However, the numerous stakeholders involved in the design and usage of the voting systems sometimes tamper with the systems thus resulting in unfavorable outcomes such as those witnessed in Kenya in 2013 and 2017 when the election results were challenged in the supreme court with the latter being nullified [8].
With mixed reactions after usage, Biometric Voter Registration in elections remains a contentious issue. Netherlands and Germany having tasted it have since stopped using it after it was shown to be unreliable. Other countries on the contrary, such as India recommend it. A 2017 study of Brazil found no systematic difference in vote choices between online and offline electorates. A group of researchers studying the recent Estonian elections describe massive operational lapses in security from transferring election results on personal thumb drives to posting network credentials on the wall in view of the public [9].
Until recently, the importance of technology for less developed countries has been ignored or paid to economic literature. During the 1960s, technological default was considered as the other side of the differences, while the problem was assumed that technology incentives in developed countries [10]. This problem is a strong infusion form of foreign technology in back countries that enable them to fill the gap of the advanced world. Recently, focus has been transferred to standard technological reasons and continuous gap between them and the advanced world. This transferee change is a central technique for development discussions, where the role of technology suppliers in the development process is very important. It seems that argument on two issues: First, refusing to reject this technology is always a good thing for backward countries, and secondly, technology agrees that the transfer of positive technology results for as answering specific questions involved in the economy can be behind Parasol [11].
In spite of these problems, the theoretical context is that support for this anxiety is still to improve the accuracy to a certain extent. This is a framework in which developed countries are relative advantage in compressed technology and innovation that can only maintain through innovation and continuous human Cαpetal quality [12]. Contrary to the opposite, less developed countries benefit from temporary competitive advantage in industries of homogeneous production and production characteristics that they can maintain unless their costs from shields and natural resources. In this framework, the channel and the mechanism are likely to transfer technology. This constant and correct distribution of scenarios cannot be able to convert this incompatible distribution of relative benefits under caliber development in a dynamic process [13].
Biometric acceptance challenges
While biometrics systems are used more and more to identify individuals and control physical and/or logical access to information, services, rights or physical spaces, questions about effectiveness of biometrics systems and “their appropriateness in widely varying contexts such as social impacts, effects on privacy, legal and policy inferences do persist”. Thomas Gurgles states that the concerns related to the human factor are major consideration of biometrics shortcomings. This is because human bodies are constantly facing physical changes, such as injury; additionally, physically challenged users may have difficulty with biometric systems based on fingerprints, hand geometry, or signature. Whereas some of the biometrics systems may be effective in their performance, they do have unforeseen operational confines hence met with both success and failure [14]. Reasons for failure do vary and are mostly hard to understand. Main characteristics of operational efficiency include error rates; speed; cost of acquisition, data security and privacy among others. Compromise must be achieved across all of these measures to achieve the best system in performance [15].
According to Jane et al. During authentication, the system matches the current pattern with the current pattern of the authenticated user. If the system fails to authenticate users trying to authenticate with their template, the system will launch a false rejection error known as the False Rejection Rate (FRR). The lower the FRR, the better the system performance [16]. On the other hand, consider the second case where user X tries to authenticate as user Y. If the system maps a user model to another user model, this is thesis as a false acceptance error. The likelihood of this error occurring is known as the False Acceptance Rate (FAR).
The lower the FAR level, the better the system performance. When a person is forced to register and the system does not allow registration, it is known as non-registration (FTE). The lower the FTE, the better the biometric systems performance. Another measure of the performance of a biometric system is the speed with which requests are processed by the system. In the environment the customer is facing, the speed of service largely determines customer satisfaction as the time it takes for the system to decide whether to accept or deny authentication is very important, especially in real-time transactions [17]. Another important factor that can lead to the acceptance of innovations in biometric technology is acceptance. McKnight argues that technological interdependence alleviates concerns that the exchange partner should act opportunistically, and Homer addresses this as the belief that others will act predictably. Accreditation is an important catalyst for the introduction of biometric technologies. Hefner went on to emphasize that users must trust the security of electronic communications for voter biometric registration technology in order to thrive and thrive. According to Matthew, accreditation is the only determinant of human participation in the introduction of biometric systems programs that process sensitive information [18].
Other studies have shown that; Strength, training, preparation, government policy, compliance, language of content, ease of use and experience determine whether a technology is accepted or rejected.
Technology is ready to determine the level of technology acceptance. Kamal and International (2012) said that for an African perspective, intention to intervene in biological innovations is somewhat influenced by stern to use such platforms, and this recovery can be considered on investment (ROI), Voltage, financial investment, and investment are examined by the psychological technology to search the platform with the relevant program. If the operation of this base investment is low, Africa is always expected to always be a tradition to communicate with the program. According to Schwyz Giblet, tools are a building that represents a degree of people, such as hate technology. Inches generally for a person, place or something positive or negative. Vasilakis et al., that some people can have a negative approval for biometric technology services and prefer them with traditional methods that exist on paper and in this case claiming the use of technology the biometric indicates the existence of an important barrier in accepting the registration of biometric technology voters.
Lighting is a process that is derived from their knowledge and skills and accumulated value of generation to another generation. According to Bons, there are three important elements of this shirt as a successful acceptance of any technology: Internet ID; Insight into the Internet; Employees with IT skills. Yeger describes as one of the problems associated with the acceptance of innovation in technology, indicating that light increases, and increases their knowledge of using online. Preparation and support for use of technology at work, Thompson.
Triantis, on the other hand, is displayed as an external environmental control. The author believes that behavior cannot occur, if prevented from material conditions in the environment or if the conditions are difficult to facilitate behavior. Policies, regulations and legal conditions are all critical conditions of technological acceptance. Resources that facilitate a person are potential barriers to accept biometric technology. According to Balsa, government policy is a committed and suitable mechanism for government policies, can confirm that individual fitness users in the field of biometric voter registration technology and this positive impact on the acceptance of biometric voter registration technology and continue learning and learning after For biometric innovations in practice, the service agreement is required with user-friendly responsibilities and valuable system.
The language of the content is also important. Biometric technology systems are usually offered in English, but Jung notes that "simple or cheap access alone does not encourage people to turn to the Internet when there is little online content in their native language." Governments should Biometric technology users are doing their part to empower software developers to ensure content online in their native language.
Ease of use “Biometric registration systems” has an impact on voter experience with the website, satisfaction and acceptance of new technological innovations. Online service users should have access to a fixed internet connection. Although the new access to Internet services has become cheaper, it is still only used by large companies. Small businesses and people not connected to the internet continue to have difficulties paying their internet subscription bills (UNESCO 2018).
IT penetration is low in Kenya, especially in rural areas (Ministry of Information Technology and Communications 2017). Knowledge contributes to the desire to adopt a new technology, and in order for customers of the core technology to see the value of a new technology, one must be aware of its potential.
Wolf, Alim, Kasaro, Namugera, and Sanim describe the adoption of biometric technology in elections. Studies were conducted in Bangladesh, Fiji, Mongolia, Nigeria, Uganda and Zambia. According to the survey, 35% of more than 130 polling places have identified biometric information recorded as part of a citizen recruitment measure. Biometric innovation is expanding throughout the hiring cycle, especially in Africa and Latin America. In 32% of countries surveyed, voter data was based on shared data. Urban framing typically includes biometric information that can be used for regulatory purposes. The results of this study also suggest that the use of biometric innovations for voter registration undermines the scope of radically different democracies. Go to Wolf et al Data Results, Expired Electoral Roll Abuse and Vote and fill in a few boxes to address the accuracy of the results. This study shows that biometric innovations are highly effective in reducing or eliminating other concepts and other democracies and creating secure, high-quality citizen ID cards. Results show that the study did not improve low enrollment rates using biometric innovations.
Whether or not biometric frameworks are used, additional measures must be taken, such as providing information about the job structure of voters, removing barriers to enrollment, and providing an overall size of enrollment. In Kenya, Jacobsen conducted a survey on private biometric enrollment focusing on another common method of government support. This study adopted a major research program for measurement. According to the survey results, voter registration in 2013 was almost free, but there were problems on Election Day and most corroboration were disappointed on Election Day, and the results were cell phones including his heavy dismissal. The Liberal Election Border Commission (IEBC), disappointingly, claimed to attract citizens over the age of 18. In 2013, we got 2 million proposals, but we found out that we only had 14.3 million (a target of 79). Of the 14.3 million registered citizens, 12.2 million (85.9) participated in the 2013 parliamentary elections and 2 million (14.09%) did not ultimately vote. On Election Day, neighboring agencies said they used an EVID (Electro-Voice Voter Identification) device that uses a unique biometric fingerprint to identify missing citizens who worked 52 hours at the monitoring station. This led to serious criticism and he did not lose any results in his political rivalry with Raila Odinga. Research shows that, like many African countries, some Kenyans do not trust their race or the IEBC. The base class has been widely politicized and has recently faced several challenges, including building trust and confidence in voters and participants to increase racial credibility. Failure to participate in certification and insurance can directly affect the process involving core components.
The importance of further development strategies and a grassroots approach to observers is increasingly evident to strategists as key to the overall reform of the information-based economy. The creation, collection and dissemination (without ambiguity or implication) of information by institutions, organizations and resources for hierarchical, human and social capital maintain a high-quality process. Information remains an important driver of significant and meaningful progress. Information is a predictable and verifiable part of logical and mechanical representations, like elements of coding, transformation, and auditing that can be communicated externally through learning, imitation, and technology. Cognitive networks also represent learning and broader insight. Raising people's hands based on both structures requires government strategists to use powerful and effective classification tools, and empirical evidence shows that new strategies are important elements of planning frameworks. These factors must be designed and optimized to overcome barriers to development.
Today's fragmentary approaches to addressing development committee strategies are characterized by a lack of meaningful reflection on the organizational and communicative nature of progress. This inappropriate positioning is Mujtahid. Each country has a broad and paradoxically powerful National Innovation System (INS). INS must guide, measure and develop the most important development barriers in the necessary development strategy. Rather than focusing solely on economic growth goals, companies focus directly on the cultural issues of strategy, research, innovation and development. He is interested in a new debate on the legitimacy of strategic arbitration. So far, there are two different views on the logic of strategic mediation in advanced writing systems. The first is a discussion of market frustration. This is useful despite the lack of adequate support for strategic communication. It therefore requires ongoing support and is a major source of frustration. It recognizes that "constructing thoughts of despair rather than showing despair helps to develop strategies later", especially in light of the fascinating problems facing each country.
Methodology
Research design
A combination of methods is used in this study. According to Shank and other research people say researchers try to understand how others should feel their experience to respond to search questions and achieve their goals. The combined research projects, which combine both quantitative and qualitative study methods, are used. The mixed methods research process suggested by Wood gate and Wilkins was followed and the nine step process was briefly explained in relation to this study. Mixed model research (concurrent)-is research in which the researcher mixes both qualitative and quantitative research approaches within a stage of the study or across two of the stages of the research process, Tashakkori and Teddlie.
Philosophy
According to Trochim et al, and Yunsey indicates a research philosophy to own researchers in the process of knowledge development. It offers insight into the values and principles of the designated research and includes issues of reality and what can be known and how they can be known. Green defines four philosophies in the use of different researcher methods: position and coating and proliferation of the eye.
Study setting and population
The study targeted Nine (9) Sub-Counties of Kisii County that comprises of 32 wards. Included in the study were County Elections Manager of IEBC, Constituency Elections Coordinators, and ICT staff working with IEBC, Other staff members working with IEBC, at least one-time electoral candidate and registered voters of Kisii County. As per the field data, 10% of total population of Kenyan cannot read and write. This study gave an approximate target population of 652,638respondents.
Sampling techniques and illustrations
Sampling is process of selecting a number of individuals or objects from a population such that the selected group contains elements representative of the characteristics found in the entire group. Mugo further explains that a sample is capable of capturing the important factors for successful Biometric Voter Registration of the defined population as long as it is properly constituted. The quality of any research is influenced by the appropriateness of methodology, instrumentation and suitability of the sampling strategy that has been adopted. Sampling techniques in this study included; purposive, stratified and simple random sampling. Table 3.1 shows a field data of the perceived population of this study. Sample size of respondents to be selected from each category.
Data processing and analysis
Before analyzing the collected data, they were first encoded. Data encryption assigns key numbers or values to each respondent group for easy entry, while data analysis involves summarizing the data collected. The information collected was quantitative and qualitative. The researcher designed simple codes to make data entry and analysis easier. Respondents' comments were numbered 1 through 5 for Section B. Collected data is collected, entered, sorted and categorized for accuracy and clarity. The data was then analyzed using an automated data analysis package known as the Statistical Package for Social Sciences 21 (SPSS). Frequency distributions were used to show the name and description of the variable, the number of repetitions of each value of the variable, and the cumulative percentage of each value associated with the variable. And the standard deviation is used to determine the accountability and validity of the data. The researcher then interprets the collected data by correlating the results with existing theories and the analysis performed according to the research questions.
Results
Descriptive statistics for user factors
The study sought to carry out dimensionality reduction due to the large amount of data under investigation. This was achieved through the use of factor analysis. However, before this data was subjected for analysis sampling adequacy assumption was checked by the use of Kaiser Meyer Olkin and Bartlett’s test of sphericity and the revealed results in Table 1 and Table 2.
Table 1: Bartlett’s test for sphericity.
From the results of table 4.1, χ² (df=990, p<.05) this means the data was sufficient for factor analysis because p-value was statistically significant at < .001.
KMO is a test to evaluate the appropriateness of the respondent’s data for factor analysis and it is recommended when the cases to value ratio is less than 1:5. It varies from 0-1 with 0.5 considered appropriate for factor analysis. Also, from the results of table 4.2 which was middling, it was revealed that there was sampling adequacy considering the KMO overall value which was .757, meaning that the data was acceptable to be subjected for further analysis (Table 2).
Table 2: KMO measure of sampling adequacy.
The researcher sought to determine the characteristics of the user factors and the perceived usefulness, perceived ease of use and BVR technology acceptability. This was achieved by the use of exploratory factor analysis as presented in Table 3. These results reveal that most of the exogenous variables were statistically significant based on Z-score whose values were above-1.96 and+1.96 and p<.05.
However, most factor of Payback and exactitude would not be significant because of their Z-score were below-1.96 and+1.96 and the p<.05.
Table 3: Factor loadings.
From Table 3 on factor loadings, it was revealed that of the seven exogenous variables of the payback factor, only two were significant. Most respondents agreed with the fact that BVR Technology causes better access to information by users and that it minimizes government bureaucracy. However, most respondents were not satisfied with the fact that; BVR Technology decreases levels of corruption, BVR Technology increases government transparency, BVR Technology reduces cost of service delivery, increases government transparency, brings greater convenience, reduces cost of service delivery and leads to faster service delivery. Also, to exactitude, respondents agreed to the common perception or belief that make people shy away from use BVR Technology as follows; Information provided is not kept confidential, BVR Technology are prone to fraud and that men are more of computer literacy than women. The study would not justify the significance of BVR Technology being prone to error, technology being difficult to use, manual systems giving better control over information and that BVR technology do not add any assistance/worth to users.
Determination of number of factors
The scree plot was used to determine the number of factors that could be best explained by the data. From Figure 1 it was evident that twelve factors could be sufficient to explain the collected data based on the eigenvalues which loaded above .50.
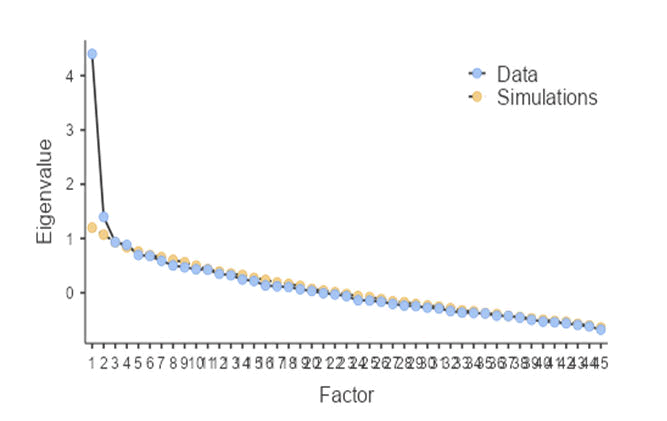
Figure 1: Scree plot
Confirmatory factor analysis
Confirmatory factor analysis helps to determine how well the exogenous variables load to a particular construct which they claim to measure. Figure 2 shows the various constructs and their measured variables.
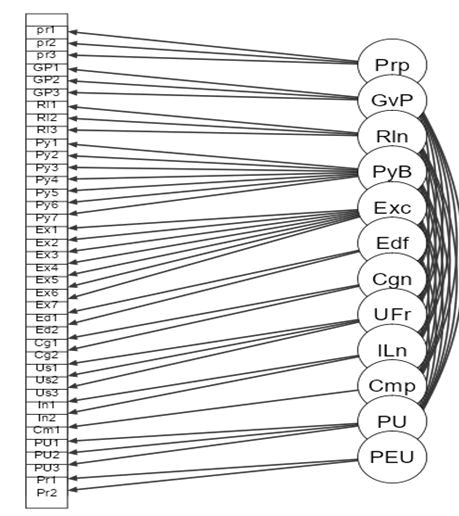
Figure 2: Confirmatory factor analysis path diagram
Figure 2 which shows corroborative component investigation way outline portrayed that every one of the deliberate factors of readiness: preparation1, preparation2, preparation3 were held since them high loadings which were over 50. A huge number concurred that Preparation in the utilization of BVR Technology will empower them use it appropriately and that it is simple for them to get planning in the Biometric Voter Registration Technology. Further they showed that it was fundamental for them to get readiness in the utilization of BVRT Technology. Similarly, the qualities of Government Policy were likewise held since they had a worth higher than 0.5. This infers that help from the Government of Kenya makes it simple for the respondents to utilize BVR Technology and the nation upholds the utilization of BVR Technology framework. Maintenance of Government Policy3 attested that it was vital for the clients to get support from the public authority on utilization of Biometric BVT Technology.
On the factor of Reliance all the three tenets had significant influence on technology acceptance. It was felt that it is necessary for the users to have confidence in the electoral body on use of BVR Technology as a way of boosting acceptance levels and also reliance on the internet to use BVR technology was paramount. Users also felt that it was safe and secure and comfortable for them to use the BVR technology. All the seven Paybacks were sustained in the elimination test and these were. This means that BVR technology decreases the levels of corruption and increases the levels of transparency. Further the finding confirmed that BVR technology leads to faster service deliver thus saving time.
Most respondents held the view that BVR Technology adds much returns to the users. It was also established that, there were more men in computer literacy than women. The other constructs of Exactitude had much significance as all the seven confirmed statistical significance. On the other hand, it was seen necessary that prior skills in computer operations are important with embracing BVR Technology. It was further realized in the thesis development that prior skills in using the internet are as important in BVR Technology.
The construct of Cognizance retained indicated that it was necessary to be aware of the BVR Technology in order for to use it. The fact of Cognizance of the BVR enabling its use could also be sustained.
In terms of User-friendliness, it was affirmed that access to Government Policy services in BVR Technology enables them to use it with a lot of ease and they had no difficulty in accessing and using the BVR Technology. This demonstrates that with User-friendliness to BVR user technology then the users are in a position to use it without encountering any difficult. Further the use of Indigenous language in BVR technology made it easier for the users to adopt and use the system in voting. Therefore, was necessary to provide the BVR technology in the Indigenous language because of the illiteracy levels and in order to increase the level of understanding and acceptability. On Compatibility the level of agreement was significant and most of the respondents did affirm that BVR Technology compatible with their work
Perception was considered to be a moderating variable in this study and it was meant to measure the extent of perceived use and that of perceived ease to use. In terms of perceived usefulness all constructs loaded significantly above 0.5 and therefore all of them were retained for further analysis. The implication of this retention is that use of online BVR Technology will enable the user to do assignment more quickly and BVR Technology makes it easier for the stakeholders to conduct the entire voting process and finally BVR Technology is useful in an electoral period. In regard to the factor of perceived ease of use two constructs were retained which means that they consented to the fact that voter registration to use BVR technology was easy for them and they actually found BVR technology flexible to interact with. This perception is critical and contributes significantly towards acceptance of the BVR technology.
Effect of the moderating variable on the relationship between the independent variable and the dependent variable
The directing variable was remembered for the model to decide the impact it has on the connection between the free factors and the reliant variable. The outcomes demonstrated that the directing variable generally had the option to impact up to .052 units of client acknowledgment, and that implies that the directing variable had a measurably certain critical impact. The discoveries uncovered that within the sight of seen handiness and the apparent convenience, a critical impact was felt. Table 4 shows the impact of the directing variable which is TAM on the connection between the free factors of the review and the reliant variable (User Acceptance).
Table 4: Outer loadings of the final model and the mediating variable.
Then again, saw convenience had an insignificant impact on the grounds that a unit change in this factor just caused an adjustment of the BVR Technology acknowledgment of .003. Additionally, the beta b esteems show that apparent usability just represented a minor 0.3% which is thought of as entirely irrelevant or peripheral. The P-worth of .945 was more than .05 importance level inferring that the impact of seen usability was genuinely inconsequential. Table 4 shows the impact of the directing variable (TAM) has on the relationship which exists between the different free factors (Preparation, Reliance, Compatibility , exactitude, Cognizance , User-invitingness, Compatibility , Government strategy and compensation) and the reliant variable (User Acceptance).
Discussion
The study affirmed that usage factors with valuable loadings that can lead to consumer acceptance of BVR technology were reliance, government policy, paybacks, edification, preparation, Cognizance , user-friendliness, Compatibility , indigenous language and exactitude. These factors in a sense have contributed significantly to the ease of adoption and usage of technology in Kenya scenario. The study affirmed that there is low usage rate of BVR Technology in Kenya as presented in chapter four due to lack of paybacks, lack of reliance, negative exactitudes of end users, inadequacy of government policy, lack of preparedness in BVR Technology and lack of edification in internet use. However, if these factors could be improved upon wide adoption and acceptability is likely to be witnessed in Kenya.
The researcher therefore recommends that Preparation of BVR Technology end users should be highly encouraged throughout the implementation of BVR Technology if these services are to be adopted and this should be done before, during and after the implementation of any BVR Technology endeavor to subdue the possibility of its failure and increase paybacks from adoption and usage of the services. The research found that preparation had a significant effect on perceived usefulness; therefore, the Ministry of ICT when intending to offer BVR Technology-services should address the preparation needs of the end users (especially preparation in the specific BVR Technology service/software) and provide continuous government policy if they want those services to be adopted successfully.
Conclusion
Implementation of BVR Technology should focus on changing the negative exactitudes of consumers towards BVR Technology. Results revealed that respondents’ negative exactitude towards BVR technology deterred them from using the services; also, validation results showed that preparation had a significant effect on perceived usefulness. This research therefore recommends that preparation be undertaken to reduce on such negative exactitudes before implementing BVR Technology and other BVR Technology because this is one of the main barriers for BVR Technology adoption.
Finally, a policy for BVR Technology and BVR Technology adoption needs to be formulated and implemented that will address end user issues. This can guide BVR Technology service providers in implementation of the BVR Technology -services and ensure successful adoption.
References
- Adam W, Peggy N, Man FL (2018) Factors that affect the acceptance of new technologies in the workplace: a cross case analysis between two universities Dimitra Skoumpo Northumbria. Int J Educ Dev Using Inf (IJEDICT) 14:209-222.
- Aqil Burney, NadeemMahmood (2006) Inductive and Deductive Research Approach. Lecture delivered on 06-03-2008 at Auditorium ofFaculty of Arts and Science, University of Karachi, Karachi, Pakistan
- Arpaci I, Yardimci YC, Ozkan S, Turetken O (2012) Organizational adoption of information Technology: A literature review. Int J eBus eGovernment Stud 4:37-50.
- Ashbourn J (2004) Where we really are with biometrics. Biometric Technology Today 12:7-9.
[Crossref] [Google Scholar].
- Azza A, John W (2015) How is technology accepted by users? A review of technology acceptance models and theories. Proceedings of the IRES 17th international conference, London, United Kingdom.
- Bagozzi RP (2013) The legacy of the technology acceptance model and a proposal for a paradigm shift. J Assoc Inf Syst 8:244-254.
- Chau A, Stephens G, Jamieson R (2004) Biometrics acceptance-perceptions of use of biometrics. ACIS 2004 Proceedings 28.
- Electronic Privacy Information Center (EPIC), Biometrics Identifiers. 2017.
- Emanuel AM Mjema (2013) Analysis of Factors Affecting Technological Innovativeness in Engineering Enterprises In Tanzania College of Engineering and Technology. Tanzan J Sci Technol (TJET) 34.
[Crossref] [Google Scholar].
- Karatzouni S, Furnell SM, Clarke NL, Botha RA (2007) Perceptions of user authentication on mobile devices. In Proceedings of the ISOneWorld Conference, Las Vegas, USA 11-13.
- Mugenda OM, Mugenda AG (2003) Research methods: Quantitative and Qualitative methods. Open Access Library J 3.
- Mulumba MA (2012) Biometric authentication systems and service delivery in healthcare sector in Kenya (Doctoral dissertation).
- Mukunth, Vasudevan (2017) "Ten Questions worth Asking About EVM Tampering". The Wire.
- Prabhakar S, Pankat S, Jain AK (2003) Biometric Recognition: Security and Privacy Concern. IEEE Transactions on Security and Privacy 1:33-42.
[Crossref] [Google Scholar].
- Rogers EM (2003). Diffusion of Innovations. (5th Edition). Free Press, New York; USA. RSA. 2016. The current state of cybercrime.
- Ruggles T (2002) Comparison of Biometric Technique. Information Science 339.
- Peggy N, Man FL (2018) Factors that affect the acceptance of new technologies in the workplace: a cross case analysis between two universities Dimitra S. and Northumbria University. Int J Educ Dev (IJEDICT) 14:209-222.
- Venkatesh V, Morris MG, Davis GB, Davis FD (2003) User acceptance of information technology: Toward a unified view. MIS Quarterly 27:425-478.
[Crossref] [Google Scholar].
 Spanish
Spanish  Chinese
Chinese  Russian
Russian  German
German  French
French  Japanese
Japanese  Portuguese
Portuguese  Hindi
Hindi 