Research Article, J Nucl Ene Sci Power Generat Technol Vol: 11 Issue: 6
Security Enhanced CTS Image Watermarking Technique using Combined DWT-DCT
Ravi Prasad Ravuri*
Department of Computer Engineering, Sriven Technologies, Virginia, United States
*Corresponding Author:Ravi Prasad Ravuri Department of Computer Engineering, Sriven Technologies, Virginia, United States; E-mail: meetravi3@gmail.com
Received date: 09 February, 2022, Manuscript No. JNPGT-22-48983; Editor assigned date: 11 February, 2022, PreQC No. JNPGT-22-48983 (PQ); Reviewed date: 25 February, 2022, QC No. JNPGT-22-48983; Revised date: 13 April 2022, Manuscript No. JNPGT-22-48983 (R); Published date: 04 May 2022, DOI: 10.4172/2325-9809.1000293
Citation: Ravi PR (2022) Security Enhanced CTS Image Watermarking Technique using Combined DWT-DCT. J Nucl Ene Sci Power Generat Technol 11:6.
Abstract
A Cheque Truncation System (CTS) expedites the clearing of cheques. The CTS electronically transmits a security deposit cheque to the drawee branch. Attackers can corrupt data and duplicate or diminish the peculiarity of the cheque. Consequently, security and privacy are critical. Therefore, the security and copyright protection of cheque is essential. In this paper, a digital watermarking technique that combines DWT and DCT for copyright protection and cheque image security has been proposed. The proposed method provides better resilience, efficacy, and is unnoticeable to the watermarked image, and it obtains a high PSNR value. Additionally, it may safeguard the information even after it has been decrypted.
Keywords: Check truncation system; Digital watermarking, Discrete wavelet transform, Discrete cosine transform, Embedding process
Introduction
A digital watermark is a translucent mark incorporated in an image that can be used for a variety of applications such as feature selection and intellectual property protection [1]. With the advancement of transmission systems, data is being transferred at never-before-seen speeds. Simultaneously, fraudulently exploited digital media easily. As a result, intellectual property has become a major concern around the world. Digital watermarking is the solution for this issue. It is the mechanism of modifying an image by inserting another message; the image's quality is unavoidably impacted [2]. We want to keep image quality degradation to a minimum, so there is no discernible difference. The significant property of watermarking is the payload size. The false positive rate for watermarking systems should be kept to a minimum. The last requirement is toughness. During the lifetime of a watermarked work, it is frequently altered, either by communication over the channel.
A strong watermark should be resistant to printing and scanning in addition to adding additive Gaussian noise. Every watermarking system has appealing characteristics. The application of the watermarking system forces us to accept tradeoffs between some of these properties. The first, and perhaps most important, characteristic is efficacy. The likelihood of correctly detecting the message in a watermarked image [3]. This probability should ideally be 1. Image fidelity is also important in watermarking. The efficient watermarking technique must be unnoticeable, reliable, and ensure security. In proposes the use of the DWT-DCT and AES techniques for digital image transmission in digital image transmission [4-7]. In a framework for the automated settling of cheque was created and tested. Check creation, processing, and settlement are all included in this architecture, which may be accessed through both online and physical channels. The use of image processing techniques to automate bank check verification in banking transactions.
The watermark is used to add information to digital data without making visible changes to it. A successful watermark is imperceptible and resistant to intentional or unintentional image modification [8]. Earlier watermarking algorithms are entirely spatial. This paper has been further arranged in the following way. The brief explanation about the proposed methodology has been discussed. The simulation outcomes of this proposed methodology has been shown. Finally, the conclusion of this paper has been given.
Materials and Methods
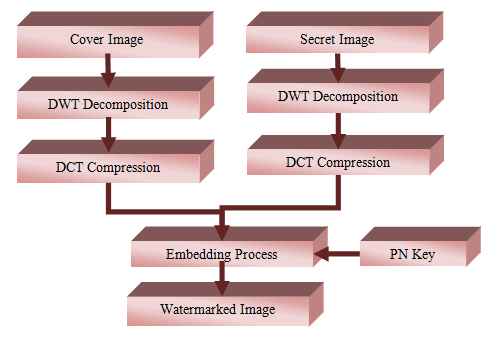
Cheque truncation is used to expedite the clearing process. For clearing house payment, the CTS transmit electronic cheque images to the drawee branch. The system is generally regarded as secure. Intruders, on the other hand, may corrupt data, degrade image quality, or duplicate the image. The importance of copyright and security cannot be overstated. Watermarks that are imperceptible can be created using DWT-DCT digital watermarking software. The flow diagram of proposed methodology for watermark embedding mechanism has been given in (Figure 1).
DWT decompositionDiscrete wavelet samples are used in decomposition transforms. It has the ability to save both position and frequency. The input image is divided into four non-overlapping sub-bands. Again, the LL1 subband is further broken down into different non-overlapping sub bands: LL2, LH2, HL2, and HH2. Watermarking in the LLx sub-band, where picture energy is concentrated, reduces image quality. The use of watermarking in these low-frequency sub-bands could improve robustness. The image boundaries and the texture characteristics of the image are present in the higher subband HHx, which is not visible to human eye. This attribute makes it possible for the watermark to be embedded without being seen. Wavelets are used to transform an image into three different spatial directions. Watermark detection at lower resolutions is computationally efficient because there are only a few frequency bands involved at each successive resolution level.
DCT CompressionA Discrete Cosine Transform (DCT) is a sum of cosine functions with discrete data points. The DCT domain has a lot of low-frequency energy. High frequencies are susceptible to assaults like as compression and scaling, while low frequencies are easily detected by the human eye. So the intermediate frequency bands were selected to avoid the most visually significant portions of the picture without being over-exposed to compression and noise. The primary benefit of DCT for watermarking is its energy compression. With this feature, you can easily insert a watermark in the image's chosen region. In tests, this method held up well against JPEG compression and considerable noise. However, the DCT on the blocks caused visual artifacts. The two dimensional DCT and IDCT can be defined as follows:
2D-DCT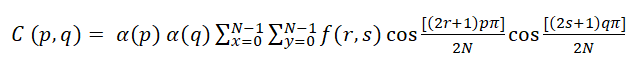
For p, q=0, 1, 2,...., N-l
For r, s=0, 1, 2,...., N-l
Where,
α(p)=1/ , p=0; α (p) =1, p=1,2,..,N-1
α(q)=1/ , q=0; α (q) =1, q=1,2,..,N-1
2D-IDCT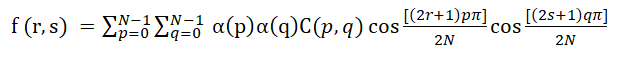
The embedding procedure of secret image into the cover image has been explained as follows:
- Choose a cover image.
- Decompose the chosen image into non-overlapping sub-bands using DWT.
- Again decompose the HL1 sub-band into four sub-bands.
- Select the HL2 sub-band and apply DCT on the same sub-band.
- Convert the watermark's greyscale image to a vector of ones and zeros.
- Create two distinct pseudorandom sequences. One sequence inserts watermark bit 0, the other bit l.
- The pseudorandom sequence has been embedded into DCT transformed HL2 sub-bands.
The embedding process has been performed using the below equation,
If the watermark bit is 1, then
Z'=Z+K * PN_1
If the watermark bit is 0 then
Z'=Z+K * PN_0
Here, Z’ represents the watermarked image, Z represents the cover image, K represents the Secret image and PN represents the Pseudorandom sequences.
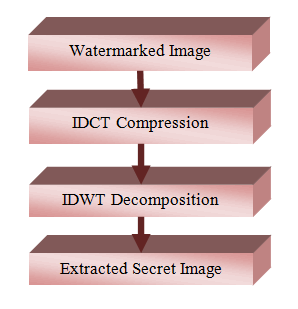
Watermark-extraction processThe watermark extraction procedure is the reverse operation of embedding process. The extraction process has been explained as follows (Figure 2):
- Get the watermarked image.
- The IDCT has been performed on the watermarked image.
- After applying DCT to each block, the middle band frequency coefficients from each block are extracted from HL2.
- Perform the 2D-IDWT on the HL2 sub-band.
- Using the same seed utilized in embedding process, generate PN_ 0 and PN l as two pseudorandom sequences and compare their middle band frequency coefficients for each HL2 sub-division block.
- Reconstruct the watermark and compare the two watermarks.
Results and Discussion
To prevent forgeries and frauds, the Reserve Bank of India (RBI) has decided to ask banks to implement additional security steps. Commercial and rural bank cheques would be the same size, according to an RBI circular distributed to all bank heads [9-12]. According to the announcement, a decision has been made to standardize cheques issued by banks across the country [13]. According to the RBI, the new attributes comprise high-quality paper, a watermark, and printing bank logos in invisible ink.
The proposed methodology was simulated using MATAB 2014 a. The following steps are used to execute the program in the MATLAB software.
Step 1: Initially run the source program file.
Step 2: Choose the cover image (cheque image).
Step 3: Choose the watermark image (logo, symbol).
Step 5: Apply 2-DWT on cover image.
Step 6: Perform the DCT on HL2 sub-band
Step 7: The cheque has been transferred to drawee of the other branch once the watermark embedding process is completed.
Step 9: After receiving the cheque image from the sender, with the help of IDCT and IDWT, the watermarked cheque image is decrypted.
Step 10: Select “Show extracted image” in the menu.
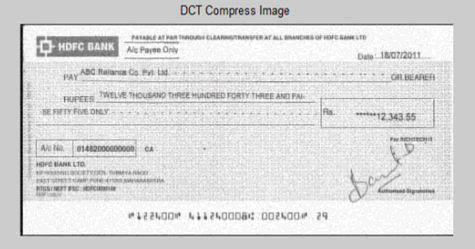
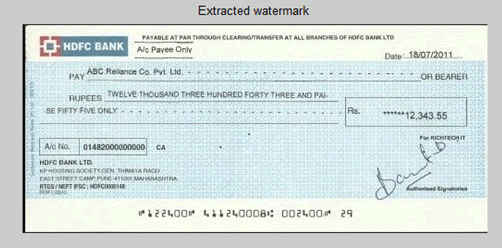
The image of the check is included into the cover. Similarly, the hidden image extracted is shown in (Figures 3-9).
The efficiency of the proposed methodology has been estimated through two different parameters which include imperceptibility and robustness [14,15]. The Peak Signal to Noise Ratio (PSNR) is a metric that determines how good a watermarked image (Figure 10 and Table 1).
| Image | PSNR (dB) | NCC |
|---|---|---|
| Image_1 | 42.25 | 0.62 |
| Image_2 | 45.87 | 0.74 |
| Image_3 | 44.39 | 0.73 |
| Image_4 | 47.58 | 0.84 |
| Image_5 | 43.01 | 0.77 |
| Average | 44.62 | 0.74 |
Table 1: PSNR and NCC values of original image.
It is used to evaluate the quality of watermarked images. It can be defined as,
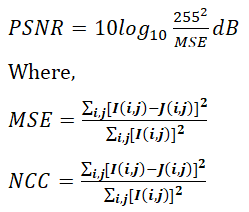
Where,
Where, I (i, j) is the host image and J (i, j) represents the watermarked image. Robustness refers to a watermark's ability to withstand various forms of digital signal processing attacks aimed at removing or degrading it. Using the Normalized correlation factor, we compared the original watermark to the watermark derived from the attacked image.
Conclusion
In this paper, the combined DCT-DWT digital watermarking technique has been explained. The DCT and DWT generate a strong and imperceptible image of the cheque. This methodology safeguards intellectual property and verifies data. This work can be extended to improve the performance and to decrease the embedding time of the proposed method. The proposed method provides better resilience, efficacy, and is unnoticeable to the watermarked image, and it obtains a high PSNR value. Additionally, it may safeguard the information even after it has been decrypted.
References
- Singh N, Kumar T, Vardhan M (2021) Blockchain-based e-cheque clearing framework with trust based consensus mechanism. Cluster Comput 24: 851-865. [Crossref][Google Scholar][Indexing at]
- Agrawal P, Chaudhary D, Madaan V (2021) Automated bank cheque verification using image processing and deep learning methods. Multimed Tools Appl 80: 5319-5350. [Crossref][Google Scholar][Indexing at]
- M Kalaiyarasi, B Perumal, M Pallikonda Rajasekaran (2020) A quantitative assessment of speckle noise reduction in SAR images using TLFFBP neural network. Arabian J Geosci 13: 1-17. [Crossref][Google Scholar][Indexing at]
- Yeung MM, Mintzer F (1997) An invisible watermarking technique for image verification. InProceedings of international conference on image processing. IEEE 2: 680-683. [Crossref][Google Scholar][Indexing at]
- Potdar VM, Han S, Chang E (2005) A survey of digital image watermarking techniques. InINDIN'05. 2005 3rd IEEE International Conference on Industrial Informatics. IEEE 709-716. [Crossref][Google Scholar][Indexing at]
- Wong PH, Au OC, Yeung YM (2003) Novel blind multiple watermarking technique for images. IEEE transactions on circuits and systems for video technology 13: 813-30. [Crossref][Google Scholar][Indexing at]
- Lee SJ, Jung SH (2001) A survey of watermarking techniques applied to multimedia. InISIE 2001. 2001 IEEE International Symposium on Industrial Electronics Proceedings. IEEE 1: 272-277. [Crossref][Google Scholar][Indexing at]
- Mohanarathinam A, Kamalraj S, Prasanna Venkatesan GK, Ravi RV, Manikandababu CS (2020) Digital watermarking techniques for image security: A review. J Ambient Intelligence Humanized Comput 11: 3221-9. [Crossref][Google Scholar][Indexing at]
- Khan A, Siddiqa A, Munib S, Malik SA (2014) A recent survey of reversible watermarking techniques. Inform Sci 279: 251-72. [Crossref][Google Scholar][Indexing at]
- Singh P, Chadha RS (2013) A survey of digital watermarking techniques, applications and attacks. Int J Eng Innov Technol 2: 165-75.
- Hartung F, Kutter M (1999) Multimedia watermarking techniques. Proceedings of the IEEE 87: 1079-107. [Crossref][Google Scholar][Indexing at]
- Lee CH, Lee YK (1999) An adaptive digital image watermarking technique for copyright protection. IEEE 45: 1005-15. [Crossref][Google Scholar][Indexing at]
- Craver S, Memon N, Yeo BL, Yeung MM (1998) Resolving rightful ownerships with invisible watermarking techniques: Limitations, attacks, and implications. IEEE 16: 573-86. [Crossref][Google Scholar][Indexing at]
- Sharkas M, ElShafie D, Hamdy N (2005) A dual digital-image watermarking technique. InWEC (5). 136-139. [Crossref][Google Scholar][Indexing at]
- Caldelli R, Filippini F, Becarelli R (2010) Reversible watermarking techniques: An overview and a classification. EURASIP J Inform Secur 2010: 1-9. [Crossref] [Google Scholar][Indexing at]
 Spanish
Spanish  Chinese
Chinese  Russian
Russian  German
German  French
French  Japanese
Japanese  Portuguese
Portuguese  Hindi
Hindi